Objects in Mini Mouse Macro
Objects in Mini Mouse Macro are central to defining conditions and actions in your macros. These objects are evaluated using operators to determine the flow and execution of your automation tasks.
Table of Contents
- BOOLEAN VARIABLE
- CLIPBOARD
- DATE
- DECIMAL VARIABLE
- DETECT IMAGE
- FILE
- FILE HASH
- FILE SIZE
- FOLDER
- FOLDER FILE COUNT
- FOLDER SIZE
- IDLE
- INTEGER VARIABLE
- KEYBOARD KEYPRESS
- LAST CONDITION
- MOUSE POSITION EQUALS
- MOUSE POSITION NEAR
- NETWORK HOST PING REPLY
- NETWORK PACKET DETECTED
- OCR
- PIXEL COLOR
- PIXEL RANGE
- PIXEL VARIABLE
- PROCESS ID
- PROCESS NAME
- RECEIVE UDP PACKET STRING
- STRING VARIABLE
- TCP PORT OPEN
- TIME
- TIME AND DATE
- WINDOW TITLE
BOOLEAN VARIABLE
Boolean variables represent a binary state: TRUE or FALSE. They are commonly used to control macro flow based on the success or failure of conditions or actions. In Mini Mouse Macro, boolean variables can be defined, evaluated, and modified dynamically within the macro.
For detailed information and use cases on boolean variables, go to the Boolean Variables page.
Purpose
Boolean variables are particularly useful for tracking binary states, such as:
- Whether a specific condition has been met.
- Controlling loop iterations.
- Managing state flags in multi-condition scenarios.
How It Works
- Boolean variables are defined using the
DEFINE BOOLEAN VARIABLEaction. - They can be evaluated using operators like
IS TRUEorIS FALSE. - Boolean values can be toggled or reset dynamically during macro execution.
Parameters
- Variable Name: The name of the boolean variable.
Operators for Evaluation
Boolean variables can be evaluated using the following operators:
- IS TRUE: Checks if the variable is
TRUE. - IS FALSE: Checks if the variable is
FALSE.
Operator Examples
IS TRUE: Ensures the variable holds a true state.
1 | IF | BOOLEAN VARIABLE | %IsActive% | IS TRUE | RUN ACTION | MESSAGE PROMPT | Task Active.- Verifies if
%IsActive%isTRUEand triggers a message prompt if so.
- Verifies if
IS FALSE: Validates that the variable is false.
1 | IF | BOOLEAN VARIABLE | %IsPaused% | IS FALSE | RUN ACTION | RESUME MACRO- Ensures
%IsPaused%isFALSEbefore resuming the macro.
- Ensures
Example: Basic Boolean Check
1 | RUN ACTION | DEFINE BOOLEAN VARIABLE | %IsComplete%::FALSE
2 | IF | BOOLEAN VARIABLE | %IsComplete% | IS FALSE | MESSAGE PROMPT | Task not complete.
3 | RUN ACTION | DEFINE BOOLEAN VARIABLE | %IsComplete%::TRUE
4 | IF | BOOLEAN VARIABLE | %IsComplete% | IS TRUE | MESSAGE PROMPT | Task completed!
Explanation - Boolean Variable Usage
- Line 1: Defines a boolean variable
%IsComplete%and sets it toFALSE. - Line 2: Checks if
%IsComplete%isFALSE, then displays a prompt indicating the task is incomplete. - Line 3: Updates
%IsComplete%toTRUE. - Line 4: Confirms the task is complete and displays a corresponding prompt.
Example: Input Box Decision Flow
* | Define the Input Box and Boolean Variable
* | ***
1 | RUN ACTION | INPUT BOX | Would you like to start (Y/N)::Start::PROMPT_YES_NO::%UserChoice%
* | ***
* | Evaluate User Input and Control Flow
* | ***
2 | IF | BOOLEAN VARIABLE | %UserChoice% | IS FALSE | THEN
3 | RUN ACTION | MESSAGE PROMPT | Ok - Macro is cancelled. UserChoice is FALSE: %UserChoice%
4 | RUN ACTION | STOP
5 | IF | ELSE
6 | RUN ACTION | MESSAGE PROMPT | Starting Macro...
7 | IF | END IF
Explanation - Input Box Decision Flow
- Line 1: Triggers an input box prompting the user with the question “Would you like to start (Y/N)” and stores the response in
%UserChoice%. - Line 2: Evaluates
%UserChoice%to check if it isFALSE(indicating the user selected “No”). - Line 3: Displays a message prompt indicating that the macro is cancelled and outputs the value of
%UserChoice%. - Line 4: Stops the macro execution.
- Line 5: Executes if
%UserChoice%is notFALSE(indicating the user selected “Yes”). - Line 6: Displays a message prompt indicating that the macro is starting.
- Line 7: Ends the conditional block.
CLIPBOARD
The clipboard object evaluates the contents of the system clipboard. It is an essential feature for macros that involve text manipulation, data extraction, or temporary storage.
Purpose
- Interact with text copied to the clipboard.
- Perform operations based on clipboard content.
- Automate repetitive tasks involving clipboard data.
Parameters
- Clipboard Content: The text or data stored in the clipboard.
How It Works
- Evaluate clipboard content using operators like
TEXT CONTAINSorTEXT IS. - Use the clipboard as a source for variable definitions.
- Perform conditional actions based on clipboard content.
- The internal variables
%CLIPBOARD%and%CLIPBOARD_LISTFILES%store clipboard data.%CLIPBOARD%stores the raw clipboard data.%CLIPBOARD_LISTFILES%stores a list of full file paths for files copied to the clipboard.
Operators for Evaluation
Clipboard objects support the following operators:
- TEXT IS: Checks if the clipboard content matches a specified string.
- TEXT CONTAINS: Verifies if a substring exists within the clipboard text.
- FILE PATH IS: Determines if the clipboard content is an exact file path.
- FILE PATH CONTAINS: Validates if the clipboard content includes a substring of a file path.
- CONTAINS A SINGLE FILE: Checks if the clipboard holds only one file.
Operator Examples
TEXT IS: Matches exact text.
1 | IF | CLIPBOARD | TEXT IS | "Exact Match" MESSAGE PROMPT | Exact text found.TEXT CONTAINS: Searches for a substring.
1 | IF | CLIPBOARD | TEXT CONTAINS | "Hello" | MESSAGE PROMPT | Found "Hello" in clipboard.FILE PATH IS: Ensures the clipboard contains an exact file path.
* | ************************************************************ * | If Clipboard contains the _MASTER.txt file path, copy it to the master folder and append the counter variable. * | Loop indefinitely with a 1-second delay. * | ************************************************************ 1 | DEFINE INTEGER VARIABLE | %Counter%::1 * | START LOOP 1 | IF | CLIPBOARD | FILE PATH IS | "D:\Backup\_MASTER.txt" | THEN 2 | RUN ACTION | COPY FILE | D:\Backup\_MASTER.txt | D:\Backup\Master\MASTER_%Counter%.txt 3 | RUN ACTION | DEFINE INTEGER VARIABLE | %Counter%::%Counter%+1 4 | RUN ACTION | WAIT SECONDS | 1 5 | IF | END IF * | END LOOP 6 | RUN ACTION | GOTO MACRO LINE | START LOOPCONTAINS A SINGLE FILE: Checks for a single file entry.
1 | IF | CLIPBOARD | CONTAINS A SINGLE FILE | COPY FILE | D:\Backup\
Example: Clipboard Text Check
1 | IF | CLIPBOARD | TEXT CONTAINS | "Important" | MESSAGE PROMPT | Found "Important" in clipboard text.
2 | IF | CLIPBOARD | TEXT IS | "Exact Match" | OUTPUT TO FILE | C:\log.txt::APPEND::Clipboard matches.
Explanation - Clipboard Usage
- Line 1: Checks if the clipboard contains the word “Important” and displays a message if true.
- Line 2: Verifies if the clipboard text matches “Exact Match” and appends a log entry to a file if true.
Advanced Example: Define Variables from Clipboard
1 | RUN ACTION | DEFINE STRING VARIABLE | %ClipText%::%CLIPBOARD%
2 | MESSAGE PROMPT | Clipboard content is: %ClipText%
- Line 1: Defines a string variable
%ClipText%with the current clipboard content. - Line 2: Displays the clipboard content in a message prompt.
DATE
Purpose
The DATE object evaluates conditions based on the current system date. It allows for decisions and actions within a macro based on specific date comparisons, enabling dynamic macro behavior.
How It Works
- The
DATEobject compares a specified date to the current system date. - Operators determine if the specified date is equal to, not equal to, before, or after the current date.
- Supports integration with other macro elements for conditional logic.
Operators for Evaluation
The following operators are supported for DATE objects:
- IS: Checks if the date matches the specified value.
- IS NOT: Checks if the date does not match the specified value.
- IS BEFORE CURRENT DATE: Checks if the specified date is before the current system date.
- IS AFTER CURRENT DATE: Checks if the specified date is after the current system date.
Operator Examples
- IS: Validates if the date matches a specific value.
- IS NOT: Confirms the date does not match a specific value.
- IS BEFORE CURRENT DATE: Checks if a date precedes the current date.
- IS AFTER CURRENT DATE: Validates if a date is later than the current date.
Example: Conditional Stop Based on Date
1 | IF | DATE | 12/31/2024 | IS AFTER CURRENT DATE | THEN
2 | RUN ACTION | MESSAGE PROMPT | Future event detected: New Year's Eve 2024
3 | RUN ACTION | STOP
4 | IF | END IF
Explanation - Conditional Stop Based on Date
- Line 1: Verifies if the date is after the current system date.
- Line 2: If true, triggers a message prompt alerting the user to an upcoming event.
- Line 3: Stops macro execution for review or preparation.
Example: Task Scheduling Based on Past Dates
1 | IF | DATE | 1/1/2025 | IS BEFORE CURRENT DATE | THEN
2 | RUN ACTION | MESSAGE PROMPT | Task is overdue! Date: %DATE%
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\OverdueTasks.txt::APPEND_NEWLINE::Task overdue as of %DATE%
4 | IF | END IF
Explanation - Task Scheduling Based on Past Dates
- Line 1: Checks if a given date is in the past relative to the system date.
- Line 2: Displays a message prompt indicating the task is overdue.
- Line 3: Logs the overdue task to a file for tracking or auditing.
DECIMAL VARIABLE
Purpose
The DECIMAL VARIABLE object evaluates conditions based on decimal (floating-point) numbers. It enables precise calculations and dynamic numeric comparisons within macros.
For detailed information on decimal variables, refer the the Decimal Variables page
How It Works
- Decimal variables are user-defined or system-defined values in a floating-point format.
- These variables support mathematical operations and logical comparisons.
- They can be combined with other objects and conditions for advanced automation.
Operators for Evaluation
The following operators are supported for DECIMAL VARIABLE objects:
- IS: Checks if the variable equals a specified value.
- IS NOT: Checks if the variable does not equal a specified value.
- GREATER THAN: Validates if the variable is greater than a specified value.
- LESS THAN: Validates if the variable is less than a specified value.
- GREATER THAN EQUAL TO: Checks if the variable is greater than or equal to a value.
- LESS THAN EQUAL TO: Checks if the variable is less than or equal to a value.
Operator Examples
- IS: Validates equality with a specific value.
- IS NOT: Ensures the variable does not match a specific value.
- GREATER THAN: Confirms if a value exceeds a threshold.
- LESS THAN: Validates if a value is below a limit.
- GREATER THAN EQUAL TO: Ensures the value meets or exceeds a threshold.
- LESS THAN EQUAL TO: Confirms the value does not exceed a maximum limit.
Example: Conditional Loop Based on Decimal Threshold
1 | RUN ACTION | DEFINE DECIMAL VARIABLE | %Progress%::0.0
2 | IF | DECIMAL VARIABLE | %Progress% | LESS THAN | 1.0 | THEN
3 | RUN ACTION | MESSAGE PROMPT | Current Progress: %Progress%
4 | RUN ACTION | DEFINE DECIMAL VARIABLE | %Progress%::%Progress%+0.1
5 | RUN ACTION | WAIT SECONDS | 1
6 | IF | END IF
Explanation - Conditional Loop Based on Decimal Threshold
- Line 1: Initializes a decimal variable
%Progress%to0.0. - Line 2: Starts a loop that continues as long as
%Progress%is less than1.0. - Line 3: Displays the current progress in a message prompt.
- Line 4: Increments
%Progress%by0.1with each iteration. - Line 5: Introduces a 1-second delay to simulate progress.
Example: Validation of Decimal Ranges
1 | IF | DECIMAL VARIABLE | %SensorReading% | GREATER THAN | 100.5 | THEN
2 | RUN ACTION | MESSAGE PROMPT | Warning: Sensor reading exceeds threshold: %SensorReading%
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\SensorWarnings.txt::APPEND_NEWLINE::%SensorReading% exceeded safe limit.
4 | IF | END IF
Explanation - Validation of Decimal Ranges
- Line 1: Checks if
%SensorReading%exceeds the threshold of100.5. - Line 2: Displays a warning message if the condition is met.
- Line 3: Logs the warning to a file for tracking and diagnostics.
DETECT IMAGE
Purpose
Detect Image evaluates whether a specified image exists on the screen. This object is ideal for identifying visual elements within a user interface or game environment. It can optionally move the mouse to the detected image’s location or save the coordinates for subsequent actions.
How It Works
- The Detect Image action scans the screen or a specified region to locate the provided image file.
- It supports options such as partial matching, full-screen search, or searching within a defined area.
- When an image is found, it can:
- Move the mouse to the image location.
- Store the X and Y coordinates in variables for later use.
- The detection process allows customization through options like quick matching, full matching, and offsets for mouse movements.
Operators for Evaluation
- IMAGE FOUND: Checks if the specified image is detected on the screen.
- IMAGE NOT FOUND: Validates that the specified image is not present.
Operator Examples
IMAGE FOUND:
1 | IF | DETECT IMAGE | image path C:\images\header.bmp::match quick::move mouse no | IMAGE FOUND | MOUSE CLICK | Left click at %X% %Y%- This example checks for the image
header.bmpon the screen. If found, it saves the coordinates to variables%X%and%Y%and performs a left mouse click at that location.
- This example checks for the image
IMAGE NOT FOUND:
1 | IF | DETECT IMAGE | image path C:\images\header.bmp::match quick::move mouse no | IMAGE NOT FOUND | CONTINUE- This example verifies the absence of the image
header.bmpand continues the macro if the image is not found.
- This example verifies the absence of the image
Example: Image Detection with Actions
1 | IF | DETECT IMAGE | image path C:\File\banner.bmp::match quick::move mouse no::save to vars X Y | IMAGE FOUND | MOUSE CLICK | Left click at %X% %Y%
2 | IF | DETECT IMAGE | image path C:\File\not_found.bmp::match quick::move mouse no | IMAGE NOT FOUND | MESSAGE PROMPT | Image not detected.
Explanation - Image Detection with Actions
- Line 1: Searches for
banner.bmpon the screen. If found, it saves the coordinates to%X%and%Y%, then performs a left mouse click at those coordinates. - Line 2: Checks for
not_found.bmp. If the image is not detected, it triggers a message prompt indicating the image was not found.
FILE
Purpose
The FILE object evaluates conditions based on the state of files in the system. It is used to check for the existence, content, or specific attributes of files to control macro flow.
How It Works
- Evaluates a file’s existence or non-existence.
- Can perform actions based on whether a file contains a specific string.
- Often combined with actions like deleting, copying, or moving files.
Operators for Evaluation
- EXIST: Verifies that the specified file exists.
- NOT EXIST: Validates that the specified file does not exist.
- FILE CONTAINS STRING: Checks if the file contains a specified string value.
Operator Examples
EXIST:
1 | IF | FILE | C:\tasklog.log | EXIST | DELETE FILE | C:\tasklog.log- Checks if
tasklog.logexists. If so, deletes the file.
- Checks if
NOT EXIST:
1 | IF | FILE | C:\tasklog.log | NOT EXIST | GOTO MACRO LINE | 5
Verifies that
tasklog.logdoes not exist. If true, jumps to macro line 5.FILE CONTAINS STRING:
1 | IF | FILE | C:\notes.txt | FILE CONTAINS STRING | "Important" | MESSAGE PROMPT | Found important text.Searches
notes.txtfor the string “Important” and displays a message if found.
Example: File Existence Check
1 | IF | FILE | C:\config.ini | EXIST | MESSAGE PROMPT | Config file exists.
2 | IF | FILE | C:\config.ini | NOT EXIST | LOAD MACRO | C:\MMM\Skip.mmmacro
Explanation - File Existence Check
- Line 1: Checks if
config.iniexists. If true, displays a message. - Line 2: If the file does not exist, creates it.
FILE HASH
Purpose
The FILE HASH object evaluates the cryptographic hash of a file to verify its integrity. This ensures the file has not been altered or corrupted.
How It Works
- Reads the specified file and computes its hash using algorithms like MD5, SHA1, or SHA256.
- Compares the computed hash with a given value to determine integrity.
- Used in scenarios where file authenticity or integrity is critical.
Operators for Evaluation
- MD5 IS: Checks if the file’s MD5 hash matches a given value.
- SHA1 IS: Validates if the file’s SHA1 hash matches the specified value.
- SHA256 IS: Verifies the file’s SHA256 hash.
- SHA384 IS: Checks the file’s SHA384 hash.
- SHA512 IS: Ensures the file’s SHA512 hash matches.
Operator Examples
MD5 IS:
1 | IF | FILE HASH | C:\example.txt | MD5 IS | bfe75d55a12df081a06e463eefc7f0c5 | MESSAGE PROMPT | File is authentic.- Verifies the MD5 hash of
example.txt. Displays a message if it matches.
- Verifies the MD5 hash of
SHA256 IS:
1 | IF | FILE HASH | C:\secure.log | SHA256 IS | 9d5e3d4f87b7da58ffeddf9df6b8a7f12a1e001c22b03c4c569fd3159a6aaf55 | STOP- Checks the SHA256 hash of
secure.log. Stops the macro if it matches.
- Checks the SHA256 hash of
Example: File Hash Validation
1 | IF | FILE HASH | C:\data.json | SHA1 IS | 3f8b7e94d8e1b4c542f6f4e40d8d24b6c9b255f9 | CONTINUE
2 | IF | FILE HASH | C:\data.json | SHA1 IS NOT | 3f8b7e94d8e1b4c542f6f4e40d8d24b6c9b255f9 | MESSAGE PROMPT | Hash mismatch detected.
Explanation - File Hash Validation
- Line 1: Confirms if the SHA1 hash of
data.jsonmatches a known value and continues execution if true. - Line 2: Displays a message if the hash does not match.
FILE SIZE
Purpose
The FILE SIZE object evaluates conditions based on the size of files in bytes. It enables macros to make decisions based on file size, such as processing large files differently from small ones.
How It Works
- Compares the file size against a specified value using logical operators.
- Can be used to trigger actions like moving, deleting, or copying files based on their size.
- Supports comparison operators for greater flexibility in evaluating file sizes.
Operators for Evaluation
- IS: Checks if the file size equals a specified value.
- IS NOT: Validates that the file size does not match the specified value.
- GREATER THAN: Ensures the file size is larger than a given value.
- LESS THAN: Confirms the file size is smaller than a given value.
- GREATER THAN EQUAL TO: Checks if the file size is at least the specified value.
- LESS THAN EQUAL TO: Verifies the file size does not exceed the given value.
Operator Examples
- IS:
1 | IF | FILE SIZE | C:\example.txt | IS | 1024 | MESSAGE PROMPT | File size is 1 KB.
- GREATER THAN:
1 | IF | FILE SIZE | C:\data.log | GREATER THAN | 1048576 | DELETE FILE | C:\data.log
- Deletes
data.logif its size exceeds 1 MB.
Example: File Size Evaluation
1 | IF | FILE SIZE | C:\backup.zip | LESS THAN | 500000 | COPY FILE | C:\backup.zip | D:\Archive\backup.zip
2 | IF | FILE SIZE | C:\backup.zip | GREATER THAN | 1000000 | DELETE FILE | C:\backup.zip
Explanation - File Size Evaluation
- Line 1: Copies
backup.zipto an archive folder if its size is less than 500 KB. - Line 2: Deletes
backup.zipif its size exceeds 1 MB.
FOLDER
Purpose
The FOLDER object evaluates conditions related to the state and contents of system directories. It is commonly used to automate file organization tasks or check folder existence.
How It Works
- Verifies if a folder exists or not.
- Evaluates folder contents, such as checking for specific files.
- Can be paired with actions like creating, deleting, or iterating through folders.
Operators for Evaluation
- EXIST: Checks if the specified folder exists.
- NOT EXIST: Validates that the folder does not exist.
- FILES CONTAINS STRING: Verifies if any file in the folder contains a specific string.
- FILES CONTAINS STRING -R: Performs a recursive check for the string in all subfolders.
Operator Examples
- EXIST:
1 | IF | FOLDER | C:\MMM\Logs | EXIST | THEN
2 | FOR | EACH | FILE IN | C:\MMM\Logs | DO
3 | RUN ACTION | OUTPUT TO FILE | C:\MMM\Logs\MASTER.log::APPEND_NEWLINE::%FILE%
4 | FOR | NEXT
5 | IF | END IF
- NOT EXIST:
1 | IF | FOLDER | D:\Audit\_tmp | NOT EXIST | RUN PROGRAM | D:\Audit\bin\logaudit.exe
- Executes logaudit.txt if
D:\Audit\_tmpfolder does not exist.
Example: Folder Existence Check
1 | IF | FOLDER | C:\Backup | EXIST | THEN
2 | RUN ACTION | MESSAGE PROMPT | Backup folder found.
3 | IF | ELSE
4 | RUN ACTION | MESSAGE PROMPT | Backup folder not found.
5 | IF | END IF
Explanation - Folder Existence Check
- Line 1: Displays a message if the
Backupfolder exists. - Line 2: Creates the
Backupfolder if it does not already exist.
FOLDER FILE COUNT
Purpose
The FOLDER FILE COUNT object evaluates the number of files in a specified folder. This is particularly useful for monitoring folder usage or triggering actions when a folder reaches a certain file count.
How It Works
- Counts the number of files in a folder, including subfolders if specified.
- Allows comparison of the file count against a specific value.
- Triggers actions based on whether the file count matches, exceeds, or falls below the given value.
Operators for Evaluation
- IS: Checks if the file count equals a specified value.
- IS NOT: Validates that the file count does not match the specified value.
- GREATER THAN: Ensures the file count exceeds the specified value.
- LESS THAN: Confirms the file count is below the given value.
- GREATER THAN EQUAL TO: Checks if the file count is at least the specified value.
- LESS THAN EQUAL TO: Verifies the file count does not exceed the given value.
Operator Examples
IS:
1 | IF | FOLDER FILE COUNT | C:\Data | IS | 10 | MESSAGE PROMPT | Folder contains exactly 10 files.GREATER THAN:
1 | IF | FOLDER FILE COUNT | C:\Data | GREATER THAN | 100 | DELETE FOLDER | C:\Data- Deletes the folder if it contains more than 100 files.
Example: Folder File Count Evaluation
1 | IF | FOLDER FILE COUNT | C:\Logs | LESS THAN | 50 | MESSAGE PROMPT | Fewer than 50 log files.
2 | IF | FOLDER FILE COUNT | C:\Logs | GREATER THAN | 100 | DELETE FOLDER | C:\Logs
Explanation - Folder File Count Evaluation
- Line 1: Displays a message if the folder contains fewer than 50 files.
- Line 2: Deletes the folder if it contains more than 100 files.
FOLDER SIZE
Purpose
The FOLDER SIZE object evaluates conditions based on the total size of a folder in bytes, including the size of its contents. This is useful for managing storage or triggering actions based on folder usage.
How It Works
- Calculates the total size of a folder, optionally including all subfolders.
- Compares the size against a specified value using logical operators.
- Triggers actions based on the result of the evaluation.
Operators for Evaluation
- IS: Checks if the folder size equals a specified value.
- IS NOT: Validates that the folder size does not match the specified value.
- GREATER THAN: Ensures the folder size is larger than a given value.
- LESS THAN: Confirms the folder size is smaller than a given value.
- GREATER THAN EQUAL TO: Checks if the folder size is at least the specified value.
- LESS THAN EQUAL TO: Verifies the folder size does not exceed the given value.
Operator Examples
GREATER THAN:
1 | IF | FOLDER SIZE | C:\Logs | GREATER THAN | 10485760 | MESSAGE PROMPT | Logs folder exceeds 10 MB.LESS THAN:
1 | IF | FOLDER SIZE | C:\Archive | LESS THAN | 5242880 | MESSAGE PROMPT | Folder size is under 5 MB.
Example: Folder Size Evaluation
1 | IF | FOLDER | C:\Backup | EXIST | THEN
2 | IF | FOLDER SIZE | C:\Backup | LESS THAN | 50000000 | THEN
3 | RUN ACTION | MESSAGE PROMPT | Backup folder is under 50 MB. Consider adding more files.
4 | IF | ELSE
5 | IF | FOLDER SIZE | C:\Backup | GREATER THAN | 100000000 | THEN
6 | RUN ACTION | MESSAGE PROMPT | Backup folder exceeds 100 MB. Archiving...
7 | RUN ACTION | OUTPUT TO FILE | C:\Backup\ArchiveLog.txt::APPEND_NEWLINE::Archived on %DATE% at %TIME%
8 | IF | ELSE
9 | RUN ACTION | MESSAGE PROMPT | Backup folder size is within acceptable limits.
10 | IF | END IF
11 | IF | END IF
12 | IF | ELSE
13 | RUN ACTION | MESSAGE PROMPT | Backup folder not found. Creating it now...
14 | RUN ACTION | FILE CREATE | C:\Backup
15 | IF | END IF
Explanation - Folder Size Evaluation
- Line 1: Checks if the folder C:\Backup exists. If it does, the macro proceeds to evaluate its size.
- Line 2: Checks if the folder size is less than 50 MB.
- Line 3: Displays a message suggesting adding more files if the folder size is under 50 MB.
- Line 4: Begins the ELSE block for when the folder size is not less than 50 MB.
- Line 5: Checks if the folder size exceeds 100 MB.
- Line 6: Displays a message indicating the folder exceeds 100 MB and simulates archiving.
- Line 7: Logs the archiving event, including the current date and time, to ArchiveLog.txt.
- Line 8: Begins the ELSE block for when the folder size is between 50 MB and 100 MB.
- Line 9: Displays a message confirming the folder size is within acceptable limits.
- Line 10: Ends the nested IF condition for folder size evaluation.
- Line 11: Ends the IF condition block evaluating folder size.
- Line 12: Begins the ELSE block for when the folder does not exist.
- Line 13: Displays a message indicating the folder was not found and will be created.
- Line 14: Creates the folder C:\Backup.
- Line 15: Ends the top-level IF condition for folder existence.
IDLE
Purpose
The IDLE object evaluates the idle state of the computer, based on a lack of user interaction or system activity. This can be used to trigger actions when the system has been idle for a certain period.
How It Works
- Monitors mouse movements, keyboard inputs, or process activity.
- Evaluates whether the system has been idle for a specified amount of time.
- Optional parameters allow customization, such as ignoring mouse or keyboard activity.
Operators for Evaluation
- IS TRUE: Confirms that the system is idle.
- IS FALSE: Validates that the system is not idle.
Operator Examples
IS TRUE:
1 | IF | IDLE | 10 | IS TRUE | MESSAGE PROMPT | System idle for 10 seconds.IS FALSE:
1 | IF | IDLE | 20 | IS FALSE | MESSAGE PROMPT | System not idle.
Example: Idle State Evaluation
1 | IF | IDLE | 120::NOMOUSE::NOKEYS | IS TRUE | MESSAGE PROMPT | System has been idle for 2 minutes.
2 | IF | IDLE | 300 | IS TRUE | OUTPUT TO FILE | C:\IdleLog.txt::APPEND_NEWLINE::Idle detected at %TIME% on %DATE%.
3 | IF | IDLE | 600 | IS TRUE | RUN PROGRAM | C:\Scripts\RestartService.bat
Explanation - Idle State Evaluation
- Line 1: Displays a message if the system has been idle for 2 minutes, ignoring both mouse and keyboard inputs.
- Line 2: Logs the idle state to a file, including the timestamp and date.
- Line 3: Runs a script to restart a service if the system remains idle for 10 minutes.
INTEGER VARIABLE
Purpose
The INTEGER VARIABLE object evaluates conditions based on the value of the local %INTEGER% variable. It provides support for numeric operations and logical evaluations, allowing precise control in macros.
For detailed information on integer variables, refer the the Integer Variable page
How It Works
- Integer variables are user-defined or system-defined values represented as whole numbers.
- They are initialized with the
DEFINE INTEGER VARIABLEaction or manipulated dynamically during macro execution. - Supports a variety of mathematical operations and conditional evaluations for advanced automation.
Operators for Evaluation
The following operators are supported for INTEGER VARIABLE objects:
- IS: Checks if the variable equals a specified value.
- IS NOT: Checks if the variable does not equal a specified value.
- GREATER THAN: Validates if the variable is greater than a specified value.
- LESS THAN: Validates if the variable is less than a specified value.
- GREATER THAN EQUAL TO: Checks if the variable is greater than or equal to a value.
- LESS THAN EQUAL TO: Checks if the variable is less than or equal to a value.
- IS EVEN: Determines if the value is an even number.
- IS ODD: Determines if the value is an odd number.
- Addition (+), Subtraction (-), Multiplication (*), Division (/), Modulus (%), and Power Of (^) are also supported.
Operator Examples
- IS: Validates if the variable matches a specific value.
- GREATER THAN: Confirms if the variable exceeds a threshold.
- IS EVEN: Checks if the variable is divisible by 2 without remainder.
- ADDITION: Adds a value to the variable.
Example: Using Mathematical Operators
1 | RUN ACTION | DEFINE INTEGER VARIABLE | %Count%::10
2 | IF | INTEGER VARIABLE | %Count% | GREATER THAN | 5 | THEN
3 | RUN ACTION | DEFINE INTEGER VARIABLE | %Count%::%Count%+5
4 | RUN ACTION | MESSAGE PROMPT | Updated Count: %Count%
5 | IF | END IF
Explanation - Using Mathematical Operators
- Line 1: Initializes the integer variable
%Count%with a value of10. - Line 2: Checks if
%Count%is greater than5. - Line 3: If true, increments
%Count%by5. - Line 4: Displays the updated value of
%Count%in a message prompt.
Example: Conditional Execution Based on Even/Odd
1 | IF | INTEGER VARIABLE | %Index% | IS ODD | THEN
2 | RUN ACTION | MESSAGE PROMPT | %Index% is an odd number.
3 | IF | ELSE
4 | RUN ACTION | MESSAGE PROMPT | %Index% is an even number.
5 | IF | END IF
Explanation - Conditional Execution Based on Even/Odd
- Line 1: Checks if
%Index%is an odd number. - Line 2: Displays a message prompt if the condition is true.
- Lines 3–4: Executes alternative logic if
%Index%is not odd (i.e., it is even).
KEYBOARD KEYPRESS
Purpose
The KEYBOARD KEYPRESS object evaluates the state of specific keys on the keyboard during macro execution. It can detect if a key is pressed or not pressed and trigger actions accordingly.
How It Works
- Monitors specific key states (pressed or not pressed) during macro execution.
- Useful for creating shortcuts, debugging, or conditional workflows.
- Requires specifying the key to evaluate.
Operators for Evaluation
- IS: Checks if a specific key is pressed.
- IS NOT: Verifies that a specific key is not pressed.
Operator Examples
IS:
1 | IF | KEYBOARD KEYPRESS | Ctrl | IS | MESSAGE PROMPT | Ctrl key is pressed.IS NOT:
1 | IF | KEYBOARD KEYPRESS | Alt | IS NOT | MESSAGE PROMPT | Alt key is not pressed.
Example: Keyboard Shortcut Evaluation
1 | IF | KEYBOARD KEYPRESS | Ctrl+S | IS | OUTPUT TO FILE | C:\Logs\ShortcutLog.txt::APPEND_NEWLINE::Shortcut Ctrl+S pressed at %TIME% on %DATE%.
2 | IF | KEYBOARD KEYPRESS | Escape | IS | STOP
Explanation - Keyboard Shortcut Evaluation
- Line 1: Logs the usage of the
Ctrl+Sshortcut to a file with a timestamp and date. - Line 2: Stops the macro if the
Escapekey is pressed.
LAST CONDITION
Purpose
The LAST CONDITION object evaluates the outcome of the most recently executed condition. This is particularly useful for branching workflows based on success or failure.
How It Works
- Evaluates whether the last condition was successful or unsuccessful.
- Acts as a debugging tool or flow control mechanism.
- Must follow a condition to be effective.
Operators for Evaluation
- SUCCESSFUL: Confirms that the previous condition was successful.
- UNSUCCESSFUL: Verifies that the previous condition failed.
Operator Examples
SUCCESSFUL:
1 | IF | FILE | C:\Logs\activity.log | EXIST | MESSAGE PROMPT | File exists. 2 | IF | LAST CONDITION | SUCCESSFUL | OUTPUT TO FILE | C:\Logs\SuccessLog.txt::APPEND_NEWLINE::Condition successful at %TIME%.UNSUCCESSFUL:
1 | IF | FILE | C:\Logs\missing.log | EXIST | DELETE FILE | C:\Logs\missing.log 2 | IF | LAST CONDITION | UNSUCCESSFUL | MESSAGE PROMPT | File not found.
Example: Conditional Logging
1 | IF | FILE | C:\Data\input.txt | EXIST | MESSAGE PROMPT | File found.
2 | IF | LAST CONDITION | SUCCESSFUL | COPY FILE | C:\Data\input.txt | C:\Backup\input.txt
3 | IF | LAST CONDITION | UNSUCCESSFUL | MESSAGE PROMPT | Missing input file.
Explanation - Conditional Logging
- Line 1: Checks if the
input.txtfile exists. - Line 2: Copies the file to a backup location if it exists.
- Line 3: Displays a message if the file is missing.
MOUSE POSITION EQUALS
Purpose
The MOUSE POSITION EQUALS object evaluates the current position of the mouse. It is useful for ensuring precise cursor placement before triggering specific actions.
How It Works
- Monitors the X and Y coordinates of the mouse.
- Compares the coordinates against specified values.
- Triggers actions based on the result of the comparison.
Operators for Evaluation
- IS: Checks if the mouse is at the specified coordinates.
- IS NOT: Verifies that the mouse is not at the specified coordinates.
Operator Examples
IS:
1 | IF | MOUSE POSITION EQUALS | {X=500, Y=300} | IS | MESSAGE PROMPT | Mouse is at position X=500, Y=300.IS NOT:
1 | IF | MOUSE POSITION EQUALS | {X=100, Y=200} | IS NOT | MESSAGE PROMPT | Mouse is not at position X=100, Y=200.
Example: Mouse Position Validation
* | Start of macro: Evaluates mouse position and performs actions accordingly.
1 | IF | MOUSE POSITION EQUALS | {X=1024, Y=768} | IS | THEN
* | Mouse is at {X=1024, Y=768}, perform a left click and log the action.
2 | RUN ACTION | MOUSE CLICK | Left click.
3 | RUN ACTION | MESSAGE PROMPT | Mouse is at 1024, 768. Click registered.
4 | IF | ELSE
* | Mouse is not at {X=1024, Y=768}, proceed to further evaluations.
5 | IF | MOUSE POSITION EQUALS | {X=0, Y=0} | IS NOT | THEN
* | Log the mouse position and define a pixel range for future checks.
6 | RUN ACTION | MESSAGE PROMPT | Mouse is not at the origin (0,0).
7 | RUN ACTION | DEFINE PIXEL RANGE VARIABLE | %PIXEL_RANGE%::At Location [X=1024 Y=768 W=50 H=50]
8 | RUN ACTION | OUTPUT TO FILE | C:\MouseLog.txt::APPEND_NEWLINE::Mouse moved to: X=%mouse_x% Y=%mouse_y%
* | Check if the system has been idle for 10 seconds without mouse or keyboard activity.
9 | IF | IDLE | 10::NOMOUSE::NOKEYS | IS TRUE | THEN
* | If idle, verify pixel range changes and alert the user.
10 | IF | PIXEL RANGE | At Location [X=1024 Y=768 W=50 H=50] | CHANGES::1::5::500 | THEN
11 | RUN ACTION | MESSAGE PROMPT | Pixel range changed while system was idle!
12 | RUN ACTION | OUTPUT TO FILE | C:\MouseLog.txt::APPEND_NEWLINE::Pixel range changed while idle at %TIME%.
13 | IF | ELSE
14 | RUN ACTION | MESSAGE PROMPT | Pixel range did not change during idle period.
15 | IF | END IF
16 | IF | END IF
17 | IF | END IF
18 | IF | END IF
* | End of macro.
Explanation - Mouse Position Validation
- Line 1: Checks if the mouse is at
{X=1024, Y=768}. If true, the block executes. - Line 2: Performs a left mouse click at
{X=1024, Y=768}. - Line 3: Displays a message confirming the mouse click at the specified position.
- Line 4: Begins the
ELSEblock if the mouse is not at{X=1024, Y=768}. - Line 5: Checks if the mouse is not at the origin
{X=0, Y=0}. - Line 6: Displays a message indicating the mouse is not at the origin.
- Line 7: Defines a pixel range variable for a 50x50 pixel area at
{X=1024, Y=768}. - Line 8: Logs the mouse position to a file.
- Line 9: Checks if the system has been idle for 10 seconds, ignoring mouse and keyboard activity.
- Line 10: Checks if there is any change in the defined pixel range during the idle period.
- Line 11: Alerts the user if a change is detected in the pixel range.
- Line 12: Logs the pixel range change to a file with a timestamp.
- Line 13: Handles the case where no change is detected in the pixel range.
- Line 14: Alerts the user that no changes were detected.
- Line 15: Ends the pixel range evaluation block.
- Line 16: Ends the idle condition block.
- Line 17: Ends the nested origin check block.
- Line 18: Ends the top-level
IFblock.
MOUSE POSITION NEAR
Purpose
The MOUSE POSITION NEAR object evaluates whether the current position of the mouse is within a specified range of a target coordinate. This is ideal for scenarios requiring approximate positioning rather than exact coordinates.
How It Works
- Monitors the X and Y coordinates of the mouse.
- Compares the coordinates against a target position with a specified tolerance.
- Can trigger actions based on whether the mouse is near or not near the target.
- The tolerance value can be customized for each axis.
Operators for Evaluation
- IS: Checks if the mouse is near the specified coordinates.
- IS NOT: Verifies that the mouse is not near the specified coordinates.
Operator Examples
IS:
1 | IF | MOUSE POSITION NEAR | {X=500, Y=300}::50::50 | IS | MESSAGE PROMPT | Mouse is near position X=500, Y=300.IS NOT:
1 | IF | MOUSE POSITION NEAR | {X=100, Y=200}::20::20 | IS NOT | MESSAGE PROMPT | Mouse is not near position X=100, Y=200.
Example: Mouse Proximity Evaluation
* | Start of macro: Evaluates if the mouse position is near specific coordinates and performs actions accordingly.
1 | IF | MOUSE POSITION NEAR | {X=1024, Y=768}::100::100 | IS | THEN
* | Mouse is near {X=1024, Y=768} within a range of 100 pixels. Perform a left click and log the event.
2 | RUN ACTION | MOUSE CLICK | Left click.
3 | RUN ACTION | MESSAGE PROMPT | Mouse is near {X=1024, Y=768}. Click registered.
4 | RUN ACTION | OUTPUT TO FILE | C:\MouseLog.txt::APPEND_NEWLINE::Mouse near {X=1024, Y=768} clicked at %TIME%.
5 | IF | ELSE
* | Mouse is not near {X=1024, Y=768}. Log and define a pixel range for further checks.
6 | RUN ACTION | MESSAGE PROMPT | Mouse is not near {X=1024, Y=768}.
7 | RUN ACTION | DEFINE PIXEL RANGE VARIABLE | %PIXEL_RANGE%::At Location [X=1024 Y=768 W=100 H=100]
* | Check for pixel range changes.
8 | IF | PIXEL RANGE | At Location [X=1024 Y=768 W=100 H=100] | CHANGES::1::5::500 | THEN
9 | RUN ACTION | MESSAGE PROMPT | Pixel range near {X=1024, Y=768} has changed.
10 | RUN ACTION | OUTPUT TO FILE | C:\MouseLog.txt::APPEND_NEWLINE::Pixel change detected near {X=1024, Y=768} at %TIME%.
11 | IF | END IF
12 | IF | END IF
* | Evaluate if the mouse is not near the origin (0,0) within a range of 50 pixels.
13 | IF | MOUSE POSITION NEAR | {X=0, Y=0}::50::50 | IS NOT | THEN
* | Mouse is not near the origin. Perform idle monitoring and log events.
14 | RUN ACTION | MESSAGE PROMPT | Mouse is not near the origin {X=0, Y=0}.
* | Check if the system has been idle for 15 seconds without mouse or keyboard activity.
15 | IF | IDLE | 15::NOMOUSE::NOKEYS | IS TRUE | THEN
* | If idle, simulate activity by moving the mouse to a defined position.
16 | RUN ACTION | MOUSE MOVEMENT | Move mouse to {X=512, Y=384}.
17 | RUN ACTION | MESSAGE PROMPT | System idle detected. Mouse moved to {X=512, Y=384}.
18 | RUN ACTION | OUTPUT TO FILE | C:\MouseLog.txt::APPEND_NEWLINE::System idle. Mouse moved at %TIME%.
19 | IF | END IF
20 | IF | END IF
* | End of macro.
Explanation - Mouse Proximity Evaluation
- Line 1: Checks if the mouse is near
{X=1024, Y=768}within a range of 100 pixels horizontally and vertically. - Line 2: Performs a left mouse click if the condition is true.
- Line 3: Displays a message confirming the mouse click near the specified position.
- Line 4: Logs the event to a file with a timestamp.
- Line 5: Begins the
ELSEblock if the mouse is not near{X=1024, Y=768}. - Line 6: Displays a message indicating the mouse is not near
{X=1024, Y=768}. - Line 7: Defines a pixel range for
{X=1024, Y=768}with a size of 100x100 pixels for monitoring. - Line 8: Checks if the defined pixel range changes within a 5-second timeout and a 500-millisecond delay.
- Line 9: Alerts the user if a change is detected in the pixel range.
- Line 10: Logs the pixel change event to a file with a timestamp.
- Line 11: Ends the
IFblock for the pixel range condition. - Line 12: Ends the
ELSEblock for the first mouse position check. - Line 13: Checks if the mouse is not near the origin
{X=0, Y=0}within a range of 50 pixels horizontally and vertically. - Line 14: Displays a message indicating the mouse is not near the origin.
- Line 15: Checks if the system has been idle for 15 seconds without mouse or keyboard activity.
- Line 16: Simulates activity by moving the mouse to
{X=512, Y=384}if the system is idle. - Line 17: Displays a message confirming the mouse movement due to detected idle state.
- Line 18: Logs the simulated mouse movement to a file with a timestamp.
- Line 19: Ends the
IFblock for the idle condition. - Line 20: Ends the top-level
IFblock for the origin check.
NETWORK HOST PING REPLY
Purpose
The NETWORK HOST PING REPLY object evaluates the reachability of a network host using ICMP ping responses. It is useful for automating tasks based on the availability of network resources.
How It Works
- Sends an ICMP ping to the specified host.
- Evaluates whether the host responds successfully or fails to respond.
- Can trigger actions based on the response status.
Operators for Evaluation
- SUCCESSFUL: Confirms that the ping reply was successful.
- UNSUCCESSFUL: Validates that the ping reply failed.
Operator Examples
SUCCESSFUL:
1 | IF | NETWORK HOST PING REPLY | 192.168.1.1 | SUCCESSFUL | MESSAGE PROMPT | Host is reachable.UNSUCCESSFUL:
1 | IF | NETWORK HOST PING REPLY | 192.168.1.1 | UNSUCCESSFUL | MESSAGE PROMPT | Host is not reachable.
Example: Network Reachability Check
* | Start of macro: Evaluates network connectivity and takes actions accordingly.
1 | IF | NETWORK HOST PING REPLY | 192.168.0.100 | SUCCESSFUL | THEN
* | Host is reachable, send a UDP packet and log the success.
2 | RUN ACTION | SEND UDP PACKET STRING | 192.168.0.100::41414::Ping Success.
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PingLog.txt::APPEND_NEWLINE::Ping successful to 192.168.0.100 at %TIME% on %DATE%.
* | Additional packet analysis: Monitor for specific incoming UDP packet content.
4 | IF | RECEIVE UDP PACKET STRING | 192.168.0.100::41414::Response::10000 | STRING FOUND | THEN
5 | RUN ACTION | MESSAGE PROMPT | Received expected UDP response from 192.168.0.100.
6 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PacketLog.txt::APPEND_NEWLINE::Valid UDP response from 192.168.0.100 at %TIME%.
7 | IF | ELSE
8 | RUN ACTION | MESSAGE PROMPT | No valid UDP response received within timeout.
9 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PacketLog.txt::APPEND_NEWLINE::No UDP response from 192.168.0.100 at %TIME%.
10 | IF | END IF
11 | IF | ELSE
* | Host is unreachable, log the failure and attempt port connectivity checks.
12 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PingFailures.txt::APPEND_NEWLINE::Host unreachable at %TIME% on %DATE%.
* | Check if TCP port 80 on the host is open.
13 | IF | TCP PORT OPEN | 192.168.0.100::80::500 | IS OPEN | THEN
14 | RUN ACTION | MESSAGE PROMPT | TCP port 80 is open on the host.
15 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PortStatus.txt::APPEND_NEWLINE::Port 80 is open on 192.168.0.100 at %TIME%.
16 | IF | ELSE
17 | RUN ACTION | MESSAGE PROMPT | TCP port 80 is closed on the host.
18 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PortStatus.txt::APPEND_NEWLINE::Port 80 is closed on 192.168.0.100 at %TIME%.
19 | IF | END IF
* | Perform a follow-up ping check after 10 seconds.
20 | RUN ACTION | WAIT SECONDS | 10
21 | IF | NETWORK HOST PING REPLY | 192.168.0.100 | SUCCESSFUL | THEN
22 | RUN ACTION | MESSAGE PROMPT | Host 192.168.0.100 is now reachable after retry.
23 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PingRecovery.txt::APPEND_NEWLINE::Host reachable on retry at %TIME% on %DATE%.
24 | IF | ELSE
25 | RUN ACTION | MESSAGE PROMPT | Host remains unreachable after retry.
26 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PingFailures.txt::APPEND_NEWLINE::Host unreachable after retry at %TIME% on %DATE%.
27 | IF | END IF
28 | IF | END IF
* | End of macro.
Explanation - Network Reachability Check
- Line 1: Checks if the host
192.168.0.100is reachable via ping. - Line 2: Sends a UDP packet to the host if the ping is successful.
- Line 3: Logs the successful ping attempt to a file.
- Line 4: Monitors for a specific UDP response from the host.
- Line 5: Displays a message if the expected UDP response is received.
- Line 6: Logs the valid UDP response to a file.
- Line 7: Begins the
ELSEblock if no UDP response is received. - Line 8: Alerts the user that no UDP response was received within the timeout.
- Line 9: Logs the failure to receive a UDP response.
- Line 10: Ends the UDP response check.
- Line 11: Begins the
ELSEblock if the host is not reachable via ping. - Line 12: Logs the ping failure to a file.
- Line 13: Checks if TCP port 80 on the host is open.
- Line 14: Displays a message if TCP port 80 is open.
- Line 15: Logs the open port status to a file.
- Line 16: Begins the
ELSEblock if TCP port 80 is closed. - Line 17: Displays a message if TCP port 80 is closed.
- Line 18: Logs the closed port status to a file.
- Line 19: Ends the port status check.
- Line 20: Waits for 10 seconds before retrying the ping.
- Line 21: Checks if the host becomes reachable after the retry.
- Line 22: Displays a message if the host is reachable after the retry.
- Line 23: Logs the recovery to a file.
- Line 24: Begins the
ELSEblock if the host remains unreachable. - Line 25: Alerts the user that the host is still unreachable.
- Line 26: Logs the failure after retry.
- Line 27: Ends the retry ping check.
- Line 28: Ends the top-level
IFblock.
NETWORK PACKET DETECTED
Purpose
The NETWORK PACKET DETECTED object evaluates network packets received on a specific interface. It is used for monitoring network activity and automating responses to packet data.
How It Works
- Monitors packets on a specified network interface.
- Evaluates packet attributes, such as source/destination address, type, or content.
- Triggers actions based on the evaluated packet attributes.
- Mini Mouse Macro creates a raw IP socket for the duration of evaluation.
- Note: This feature requires administrative privileges.
- Note: The raw IP socket is closed after the evaluation is complete.
Operators for Evaluation
- SOURCE ADDRESS: Checks the source address of the packet.
- DESTINATION ADDRESS: Validates the destination address of the packet.
- PACKET CONTAINS STRING: Verifies if the packet contains a specific string.
- PACKET TYPE TCP/UDP/ICMP: Filters packets based on their protocol type.
- PACKET COUNT TCP/UDP/ICMP/TOTAL: Counts packets based on their protocol type.
- PACKET SOURCE PORT NUMBER: Checks the source port number of the packet.
- PACKET DESTINATION PORT NUMBER: Checks the destination port number of the packet.
Operator Examples
SOURCE ADDRESS:
1 | IF | NETWORK PACKET DETECTED | Ethernet | SOURCE ADDRESS | 192.168.1.10 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PacketLog.txt::APPEND_NEWLINE::Packet received from 192.168.1.10.PACKET TYPE UDP:
1 | IF | NETWORK PACKET DETECTED | Wi-Fi | PACKET TYPE UDP | MESSAGE PROMPT | UDP packet detected.
Example: Source Address Detection
1 | IF | NETWORK PACKET DETECTED | Ethernet | SOURCE ADDRESS | 10.0.0.1 | THEN
2 | RUN ACTION | MESSAGE PROMPT | Packet from 10.0.0.1 detected.
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\SourceAddressLog.txt::APPEND_NEWLINE::Packet from 10.0.0.1 at %TIME%.
4 | IF | END IF
Explanation - Source Address Detection
- Line 1: Detects packets from the source address
10.0.0.1on the Ethernet interface. - Line 2: Displays a message prompt if a packet from
10.0.0.1is detected. - Line 3: Logs the detection event to a file with a timestamp.
Example: Destination Address Detection
1 | IF | NETWORK PACKET DETECTED | Wi-Fi | DESTINATION ADDRESS | 10.0.0.2 | THEN
2 | RUN ACTION | MESSAGE PROMPT | Packet to 10.0.0.2 detected.
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\DestinationAddressLog.txt::APPEND_NEWLINE::Packet to 10.0.0.2 at %TIME%.
4 | IF | END IF
Explanation - Destination Address Detection
- Line 1: Detects packets destined for
10.0.0.2on the Wi-Fi interface. - Line 2: Displays a message prompt if a packet to
10.0.0.2is detected. - Line 3: Logs the detection event to a file with a timestamp.
Example: Packet Type Detection
1 | IF | NETWORK PACKET DETECTED | Ethernet | PACKET TYPE TCP | THEN
2 | RUN ACTION | MESSAGE PROMPT | TCP packet detected.
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PacketTypeLog.txt::APPEND_NEWLINE::TCP packet detected at %TIME%.
4 | IF | END IF
Explanation - Packet Type Detection
- Line 1: Detects TCP packets on the Ethernet interface.
- Line 2: Displays a message prompt if a TCP packet is detected.
- Line 3: Logs the detection event to a file with a timestamp.
Example: Packet Count Detection
1 | IF | NETWORK PACKET DETECTED | Ethernet | PACKET COUNT TOTAL | GREATER THAN | 100 | THEN
2 | RUN ACTION | MESSAGE PROMPT | More than 100 packets detected.
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PacketCountLog.txt::APPEND_NEWLINE::More than 100 packets detected at %TIME%.
4 | IF | END IF
Explanation - Packet Count Detection
- Line 1: Checks if the total packet count on the Ethernet interface exceeds 100.
- Line 2: Displays a message prompt if more than 100 packets are detected.
- Line 3: Logs the detection event to a file with a timestamp.
Example: Packet Monitoring
* | Start of macro: Detect and process network packets based on specific conditions.
1 | IF | NETWORK PACKET DETECTED | Ethernet | SOURCE ADDRESS | 192.168.0.200 | THEN
* | Packet detected from source address 192.168.0.200. Send an acknowledgment and log the event.
2 | RUN ACTION | SEND UDP PACKET STRING | 192.168.0.200::41414::Acknowledged.
3 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PacketLog.txt::APPEND_NEWLINE::Packet from 192.168.0.200 acknowledged at %TIME%.
4 | IF | ELSE
* | No packets detected from 192.168.0.200. Check for packets with specific content.
5 | IF | NETWORK PACKET DETECTED | Ethernet | PACKET CONTAINS STRING | "Trigger" | THEN
* | Trigger packet detected. Log the event and analyze its contents.
6 | RUN ACTION | OUTPUT TO FILE | C:\Logs\TriggerPackets.txt::APPEND_NEWLINE::Trigger packet detected at %TIME%.
* | Perform packet analysis to extract details.
7 | RUN ACTION | OUTPUT TO FILE | C:\Logs\PacketAnalysis.txt::APPEND_NEWLINE::Analyzing packet content: "Trigger" found at %TIME%.
* | Optionally send a response if necessary.
8 | RUN ACTION | SEND UDP PACKET STRING | 192.168.0.200::41414::Trigger processed.
9 | IF | ELSE
* | No packets with the string "Trigger" were detected.
10 | RUN ACTION | MESSAGE PROMPT | No trigger packets detected on Ethernet interface.
11 | IF | END IF
12 | IF | END IF
* | Additional packet checks: Monitor for ICMP packets and analyze.
13 | IF | NETWORK PACKET DETECTED | Ethernet | PACKET TYPE ICMP | THEN
* | ICMP packet detected. Log the event and check for further analysis.
14 | RUN ACTION | OUTPUT TO FILE | C:\Logs\ICMPPackets.txt::APPEND_NEWLINE::ICMP packet detected at %TIME%.
* | Verify packet source for additional actions.
15 | IF | NETWORK PACKET DETECTED | Ethernet | SOURCE ADDRESS | 192.168.0.200 | THEN
16 | RUN ACTION | MESSAGE PROMPT | ICMP packet from 192.168.0.200 detected. No action needed.
17 | IF | ELSE
18 | RUN ACTION | MESSAGE PROMPT | ICMP packet detected from unknown source.
19 | IF | END IF
20 | IF | END IF
* | End of macro.
Explanation - Packet Monitoring
- Line 1: Detects packets on the Ethernet interface from source address
192.168.0.200. - Line 2: Sends a UDP acknowledgment packet to the detected source address.
- Line 3: Logs the acknowledgment event to a file.
- Line 4: Begins the
ELSEblock if no packets from192.168.0.200are detected. - Line 5: Checks for packets containing the string “Trigger.”
- Line 6: Logs the detection of a “Trigger” packet to a file.
- Line 7: Logs further analysis of the packet content to another file.
- Line 8: Sends a UDP packet to acknowledge processing of the “Trigger” packet.
- Line 9: Begins the
ELSEblock if no packets with the “Trigger” string are detected. - Line 10: Displays a message indicating no “Trigger” packets were found.
- Line 11: Ends the “Trigger” packet detection block.
- Line 12: Ends the source address detection block.
- Line 13: Detects ICMP packets on the Ethernet interface.
- Line 14: Logs the detection of ICMP packets to a file.
- Line 15: Checks if the ICMP packet is from source address
192.168.0.200. - Line 16: Displays a message indicating the ICMP packet is from a known source.
- Line 17: Begins the
ELSEblock for ICMP packets from unknown sources. - Line 18: Alerts the user to ICMP packets from an unknown source.
- Line 19: Ends the ICMP source check block.
- Line 20: Ends the ICMP packet detection block.
OCR
Purpose
The OCR (Optical Character Recognition) object evaluates text detected within saved images or specified areas of the screen. It is useful for automating tasks based on text content or changes in visual elements.
How It Works
- Processes an image file or a specified screen region to extract text.
- Evaluates the detected text for specific content or patterns.
- Can evaluate from a single image, a folder of images, or a screen area.
- Supports language dictionaries and custom settings for text detection.
- Can store detected text in a variable for further processing.
- Triggers actions based on text content or detection success.
Screen Evaluation
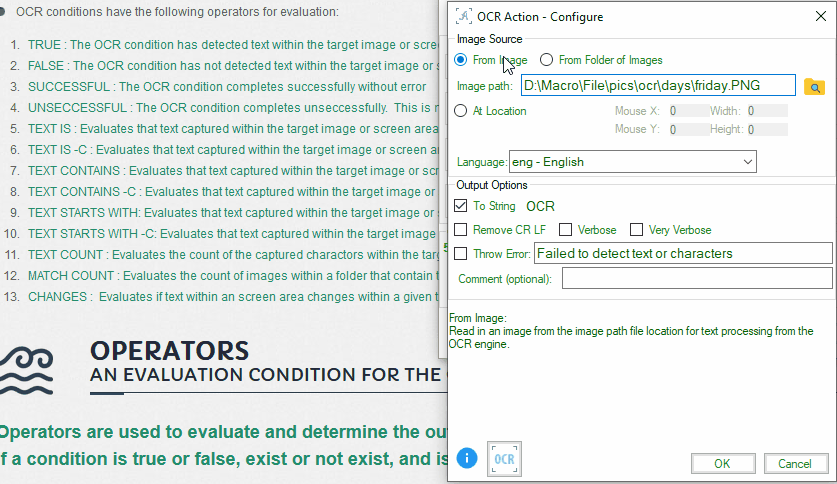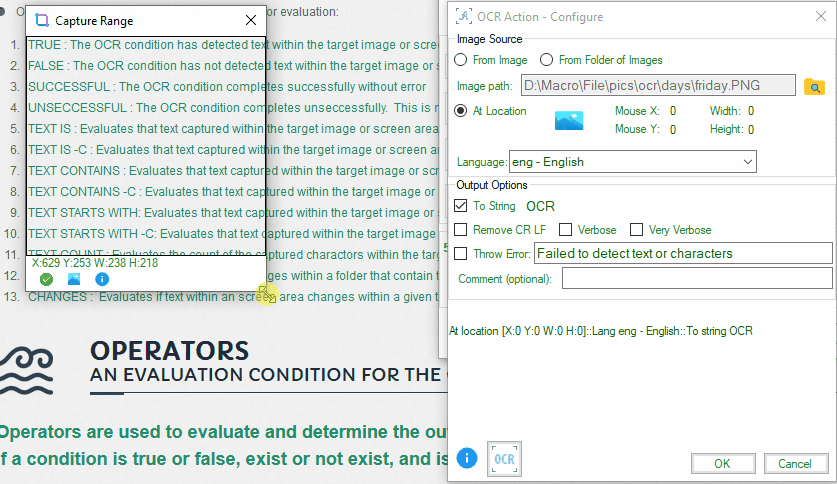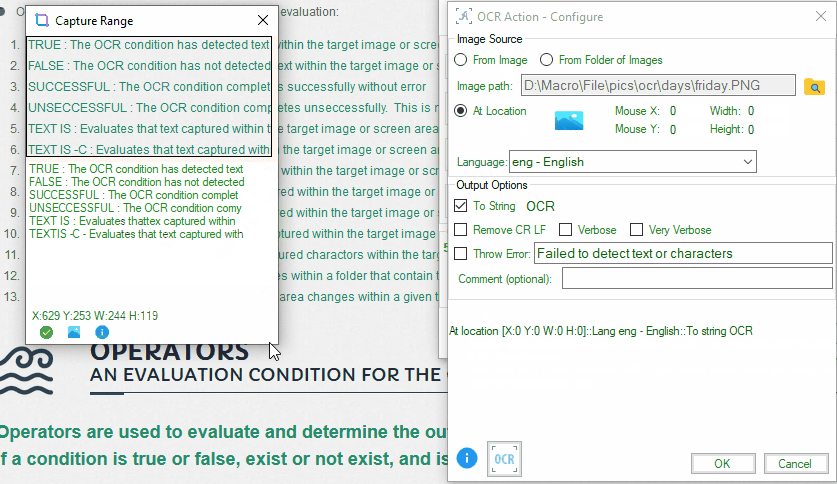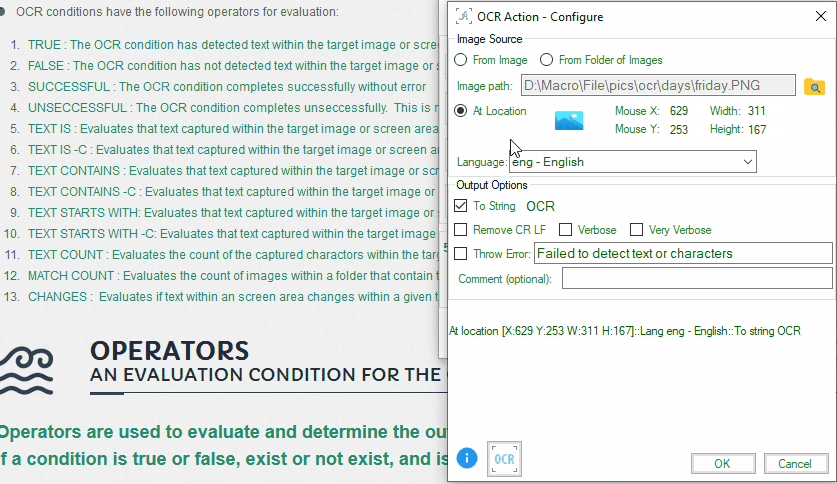
- Screen Area: Defines a rectangular area on the screen for text detection. To select a screen location for OCR, follow these steps:
- Open the ‘Add Condition’ tool and choose the OCR condition.
- Click on the ‘At Location’ image icon.
- Adjust the screen size using the mouse and the resize bar.
- Capture the desired screen area.
- Click ‘Ok’ in the bottom menu to confirm your selection.
Operators for Evaluation
- TRUE: The OCR condition has detected text within the target image or screen area.
- FALSE: The OCR condition has not detected text within the target image or screen area.
- SUCCESSFUL: The OCR condition completes successfully without error.
- UNSUCCESSFUL: The OCR condition completes unsuccessfully. This is most likely due to a syntax error or the OCR plugin not being enabled.
- TEXT IS: Evaluates that text captured within the target image or screen area matches a text value.
- TEXT IS -C: Evaluates that text captured within the target image or screen area matches a text value (case insensitive).
- TEXT CONTAINS: Evaluates that text captured within the target image or screen area contains a text value.
- TEXT CONTAINS -C: Evaluates that text captured within the target image or screen area contains a text value (case insensitive).
- TEXT STARTS WITH: Evaluates that text captured within the target image or screen area starts with a text value.
- TEXT STARTS WITH -C: Evaluates that text captured within the target image or screen area starts with a text value (case insensitive).
- TEXT COUNT: Evaluates the count of the captured characters within the target image or screen area.
- MATCH COUNT: Evaluates the count of images within a folder that contain text.
- CHANGES: Evaluates if text within a screen area changes within a given time period.
Optional Output Parameters
The OCR condition can take optional output parameters:
- To String: Capture any text from the target image or screen location to a variable. The default variable is
%OCR%. - Remove CR LF: When selected, removes any carriage return/line feed sequence (new line detections) from the captured text. This results in the captured text being a single line of text.
- Verbose and Very Verbose: Outputs additional internal MMM event log details. Useful for debugging purposes.
- Throw Error: Returns the error text and a false/failed state if no text is found.
- Comment: Adds an optional comment to the macro line.
Operator Examples
TRUE:
1 | IF | OCR | From image D:\Images\menu.png | TRUE | MESSAGE PROMPT | Text detected in menu image.FALSE:
1 | IF | OCR | From image D:\Images\menu.png | FALSE | MESSAGE PROMPT | No text detected in menu image.TEXT IS:
1 | IF | OCR | From image D:\Images\banner.png::to string OCR | TEXT IS | "Monday" | MESSAGE PROMPT | The text is Monday.TEXT IS -C:
1 | IF | OCR | From image D:\Images\title.png::to string OCR::Remove CR LF | TEXT IS -C | "hello world" | MESSAGE PROMPT | Case-insensitive match for 'hello world'.TEXT CONTAINS:
1 | IF | OCR | From image D:\Screenshots\login.png::to string OCR | TEXT CONTAINS | "User" | MESSAGE PROMPT | Login screen contains 'User'.TEXT CONTAINS -C:
1 | IF | OCR | From image D:\Screenshots\alert.png::to string OCR::Verbose | TEXT CONTAINS -C | "warning" | MESSAGE PROMPT | Case-insensitive 'warning' found.TEXT STARTS WITH:
1 | IF | OCR | At location [X=100, Y=150, W=300, H=50]::to string OCR | TEXT STARTS WITH | "Report" | MESSAGE PROMPT | Text starts with 'Report'.TEXT STARTS WITH -C:
1 | IF | OCR | At location [X=100, Y=150, W=300, H=50]::to string OCR::Remove CR LF | TEXT STARTS WITH -C | "error" | MESSAGE PROMPT | Case-insensitive 'error' detected.TEXT COUNT:
1 | IF | OCR | From image D:\Docs\text.png::to string OCR | TEXT COUNT | GREATER THAN | 100 | MESSAGE PROMPT | More than 100 characters detected.MATCH COUNT:
1 | IF | OCR | From folder D:\Screenshots\ | MATCH COUNT | GREATER THAN | 5 | MESSAGE PROMPT | More than 5 matching images detected.CHANGES:
1 | IF | OCR | At location [X=200, Y=300, W=400, H=100]::to string OCR::Verbose | CHANGES::2::5::1000 | MESSAGE PROMPT | Detected 2 text changes in 5 seconds.
Example: OCR-Based Workflow
* | Start of OCR-based macro: Detects, evaluates, and processes text from images and screen regions.
* | Step 1: Detect if a specific text exists in an image file and log the results.
1 | IF | OCR | From image D:\Screenshots\report.png::to string OCR::Remove CR LF | TEXT STARTS WITH | "Report" | THEN
* | Log detected text that starts with "Report" to a file.
2 | RUN ACTION | OUTPUT TO FILE | D:\Logs\OCRReports.txt::APPEND_NEWLINE::Report detected at %TIME% on %DATE%.
* | Check if the length of detected text exceeds a threshold.
3 | IF | OCR | From image D:\Screenshots\report.png::to string OCR | TEXT COUNT | GREATER THAN | 50 | THEN
4 | RUN ACTION | MESSAGE PROMPT | Report contains more than 50 characters.
5 | IF | END IF
6 | IF | ELSE
* | No relevant report detected; log this for reference.
7 | RUN ACTION | OUTPUT TO FILE | D:\Logs\OCRReports.txt::APPEND_NEWLINE::No relevant report found at %TIME% on %DATE%.
8 | IF | END IF
* | Step 2: Detect warnings in a specified screen area and take appropriate action.
9 | IF | OCR | At location [X=100, Y=200, W=400, H=100]::to string OCR::Verbose | TEXT CONTAINS -C | "warning" | THEN
* | Warning detected, log it and notify the user.
10 | RUN ACTION | OUTPUT TO FILE | D:\Logs\OCRWarnings.txt::APPEND_NEWLINE::Warning detected at %TIME% on %DATE%.
11 | RUN ACTION | MESSAGE PROMPT | Warning found in the monitored area!
12 | IF | ELSE
* | No warnings found, log the absence of warnings.
13 | RUN ACTION | OUTPUT TO FILE | D:\Logs\OCRWarnings.txt::APPEND_NEWLINE::No warnings detected at %TIME% on %DATE%.
14 | IF | END IF
* | Step 3: Monitor a screen area for changes in text and respond dynamically.
15 | IF | OCR | At location [X=500, Y=300, W=300, H=50]::to string OCR::Verbose | CHANGES::3::10::500 | THEN
* | Detected three or more text changes in the monitored area.
16 | RUN ACTION | MESSAGE PROMPT | Text changes detected in the monitored area!
17 | RUN ACTION | OUTPUT TO FILE | D:\Logs\OCRChanges.txt::APPEND_NEWLINE::Text changes detected at %TIME% on %DATE%.
* | Further evaluate the detected text for critical content.
18 | IF | OCR | At location [X=500, Y=300, W=300, H=50]::to string OCR::Throw Error | TEXT CONTAINS | "Critical" | THEN
19 | RUN ACTION | MESSAGE PROMPT | Critical content detected in text changes!
20 | RUN ACTION | OUTPUT TO FILE | D:\Logs\CriticalLogs.txt::APPEND_NEWLINE::Critical content found at %TIME% on %DATE%.
21 | IF | END IF
22 | IF | END IF
* | Step 4: Batch process multiple images in a folder and log matching results.
23 | IF | OCR | From folder D:\BatchScreenshots\ | MATCH COUNT | GREATER THAN | 5 | THEN
* | More than 5 matching images detected in the folder; log the result.
24 | RUN ACTION | OUTPUT TO FILE | D:\Logs\BatchOCR.txt::APPEND_NEWLINE::More than 5 matching images found at %TIME% on %DATE%.
* | Evaluate the specific images containing matches.
25 | FOR | EACH | FILE IN | D:\BatchScreenshots | DO
26 | IF | OCR | From image %FILE%::to string OCR::Verbose | TEXT CONTAINS | "Summary" | THEN
27 | RUN ACTION | OUTPUT TO FILE | D:\Logs\BatchOCRDetails.txt::APPEND_NEWLINE::Image %FILE% contains 'Summary'.
28 | IF | END IF
29 | FOR | NEXT
30 | IF | ELSE
* | Fewer than 5 matching images detected; log the result.
31 | RUN ACTION | OUTPUT TO FILE | D:\Logs\BatchOCR.txt::APPEND_NEWLINE::Fewer than 5 matching images found at %TIME% on %DATE%.
32 | IF | END IF
* | End of macro.
Explanation - OCR-Based Workflow
- Line 1: Checks if the text in the image
report.pngstarts with “Report”. - Line 2: Logs the detected “Report” text to
OCRReports.txt. - Line 3: Checks if the length of the detected text in
report.pngexceeds 50 characters. - Line 4: Displays a message prompt if the text length exceeds 50 characters.
- Line 5: Ends the
IFblock for the text length check. - Line 6: Begins the
ELSEblock for when the text does not start with “Report”. - Line 7: Logs that no relevant report text was found.
Line 8: Ends the
IFblock for the text starting condition.- Line 9: Checks if the word “warning” (case-insensitive) is detected in the specified screen area
[X=100, Y=200, W=400, H=100]. - Line 10: Logs the detected warning to
OCRWarnings.txt. - Line 11: Displays a message prompt notifying the user of the warning.
- Line 12: Begins the
ELSEblock for when no warnings are detected. - Line 13: Logs the absence of warnings to
OCRWarnings.txt. Line 14: Ends the
IFblock for the warning detection condition.- Line 15: Monitors a screen area
[X=500, Y=300, W=300, H=50]for three or more text changes within 10 seconds with a delay of 500 ms between checks. - Line 16: Displays a message prompt when text changes are detected.
- Line 17: Logs the detected text changes to
OCRChanges.txt. - Line 18: Checks if the detected text in the monitored area contains the word “Critical”.
- Line 19: Displays a message prompt if “Critical” is found in the detected text.
- Line 20: Logs the detection of critical content to
CriticalLogs.txt. - Line 21: Ends the
IFblock for detecting critical content. Line 22: Ends the
IFblock for monitoring text changes.- Line 23: Checks if more than 5 images in the folder
BatchScreenshotscontain matching OCR text. - Line 24: Logs the result to
BatchOCR.txtif more than 5 matches are found. - Line 25: Iterates through each file in the folder
BatchScreenshotsfor further analysis. - Line 26: Checks if each file contains the word “Summary” in its OCR-detected text.
- Line 27: Logs details of the matching image to
BatchOCRDetails.txt. - Line 28: Ends the
IFblock for matching text within an image. - Line 29: Ends the loop iterating through the files in the folder.
- Line 30: Begins the
ELSEblock for when fewer than 5 matches are found. - Line 31: Logs the result to
BatchOCR.txtfor fewer than 5 matches. Line 32: Ends the
IFblock for matching count condition.- Line 33: Marks the end of the macro.
PIXEL COLOR
Purpose
The PIXEL COLOR object evaluates the color of a specific pixel at a given screen location. This is useful for detecting UI changes, validating states, or triggering actions based on visual cues.
How It Works
- Captures the RGB (Red, Green, Blue) color values of a specific pixel.
- Compares the captured values against specified criteria.
- Triggers actions based on the evaluation result.
Operators for Evaluation
- IS THE SAME: Verifies that the pixel color matches the specified RGB values.
- IS NOT THE SAME: Ensures the pixel color does not match the specified RGB values.
- CHANGES: Detects changes in the pixel color within a defined time and delay period.
- CHANGES::X::Y::Z:
- X: The number of changes to detect.
- Y: The total time to wait for changes (in seconds). A value of 0 waits until all changes occur. At the end of the time period, the statement will evaluate to FALSE and continue.
- Z: The delay between detecting pixel changes (in milliseconds). A value of 0 skips the delay.
- CHANGES::X::Y::Z:
![]()
Pixel Color condition via the 'Add Condition' dialog window.
![]()
Choose the Pixel Color after selecting the PIXEL COLOR object. Move the mouse to the desired color or manually enter the color by clicking the text.
Operator Examples
IS THE SAME:
1 | IF | PIXEL COLOR | Color [R=145, G=228, B=247]::At Location [X=942, Y=536] | IS THE SAME | MESSAGE PROMPT | Pixel matches the specified color.IS NOT THE SAME:
1 | IF | PIXEL COLOR | Color [R=255, G=255, B=255]::At Location [X=1024, Y=768] | IS NOT THE SAME | MESSAGE PROMPT | Pixel color does not match.CHANGES:
1 | IF | PIXEL COLOR | At Location [X=500, Y=400] | CHANGES::3::10::500 | MESSAGE PROMPT | Pixel color changed 3 times within 10 seconds.
Example: Pixel Color Evaluation
* | Start of macro: Evaluates pixel colors and changes to trigger actions dynamically.
* | Step 1: Detect if a specific pixel matches a target color.
1 | IF | PIXEL COLOR | Color [R=0, G=128, B=0]::At Location [X=300, Y=400] | IS THE SAME | THEN
* | Pixel at [X=300, Y=400] matches green. Log and notify the user.
2 | RUN ACTION | MESSAGE PROMPT | Green detected at X=300, Y=400!
3 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelLog.txt::APPEND_NEWLINE::Green detected at %TIME% on %DATE%.
4 | IF | ELSE
* | Pixel does not match green; check if it is white.
5 | IF | PIXEL COLOR | Color [R=255, G=255, B=255]::At Location [X=300, Y=400] | IS THE SAME | THEN
6 | RUN ACTION | MESSAGE PROMPT | White detected at X=300, Y=400.
7 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelLog.txt::APPEND_NEWLINE::White detected at %TIME% on %DATE%.
8 | IF | ELSE
* | Pixel does not match green or white; log unknown color.
9 | RUN ACTION | MESSAGE PROMPT | Unknown color detected at X=300, Y=400.
10 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelLog.txt::APPEND_NEWLINE::Unknown color detected at %TIME% on %DATE%.
11 | IF | END IF
12 | IF | END IF
* | Step 2: Monitor a specific pixel for color changes.
13 | IF | PIXEL COLOR | At Location [X=500, Y=400] | CHANGES::2::10::500 | THEN
* | Pixel color changed twice within 10 seconds; log and notify.
14 | RUN ACTION | MESSAGE PROMPT | Pixel color changed twice at X=500, Y=400!
15 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelChanges.txt::APPEND_NEWLINE::Pixel at X=500, Y=400 changed twice at %TIME% on %DATE%.
* | Further evaluation: Check if the pixel matches red after changes.
16 | IF | PIXEL COLOR | Color [R=255, G=0, B=0]::At Location [X=500, Y=400] | IS THE SAME | THEN
17 | RUN ACTION | MESSAGE PROMPT | Red detected at X=500, Y=400 after changes!
18 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelChanges.txt::APPEND_NEWLINE::Red detected after changes at %TIME% on %DATE%.
19 | IF | ELSE
20 | RUN ACTION | MESSAGE PROMPT | No red detected after pixel changes.
21 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelChanges.txt::APPEND_NEWLINE::No red detected after changes at %TIME% on %DATE%.
22 | IF | END IF
23 | IF | END IF
* | Step 3: Evaluate pixel color across multiple locations dynamically.
24 | FOR | EACH | I | = | 1 TO 3 | DO
* | Check three locations sequentially for a specific pixel color.
25 | IF | PIXEL COLOR | At Location [X=%I%*100, Y=%I%*100] | IS THE SAME | THEN
26 | RUN ACTION | MESSAGE PROMPT | Pixel at [%I%*100, %I%*100] matches the target color.
27 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelEvaluation.txt::APPEND_NEWLINE::Pixel at [%I%*100, %I%*100] matches target color at %TIME%.
28 | IF | END IF
29 | FOR | NEXT
* | End of macro.
Explanation - Pixel Color Evaluation
- Line 1: Checks if the pixel at
[X=300, Y=400]matches the color green (R=0, G=128, B=0). - Line 2: Displays a message prompt if the pixel matches green.
- Line 3: Logs the detection of green to
PixelLog.txt. - Line 4: Begins the
ELSEblock if the pixel is not green. - Line 5: Checks if the pixel matches white (
R=255, G=255, B=255). - Line 6: Displays a message prompt if the pixel matches white.
- Line 7: Logs the detection of white to
PixelLog.txt. - Line 8: Begins the
ELSEblock if the pixel is neither green nor white. - Line 9: Displays a message prompt for an unknown color.
- Line 10: Logs the detection of an unknown color to
PixelLog.txt. - Line 11: Ends the block for detecting white.
Line 12: Ends the block for detecting green.
- Line 13: Monitors pixel at
[X=500, Y=400]for two color changes within 10 seconds, with 500 ms delay between checks. - Line 14: Displays a message prompt if two color changes are detected.
- Line 15: Logs the pixel color changes to
PixelChanges.txt. - Line 16: Checks if the pixel matches red (
R=255, G=0, B=0) after changes. - Line 17: Displays a message prompt if red is detected after changes.
- Line 18: Logs the detection of red after changes to
PixelChanges.txt. - Line 19: Begins the
ELSEblock if red is not detected. - Line 20: Displays a message prompt if no red is detected after changes.
- Line 21: Logs the absence of red detection to
PixelChanges.txt. - Line 22: Ends the block for checking red.
Line 23: Ends the block for monitoring pixel changes.
- Line 24: Starts a loop to evaluate pixel colors across three locations dynamically.
- Line 25: Checks if the pixel at dynamic locations
[X=%I%*100, Y=%I%*100]matches the target color. - Line 26: Displays a message prompt if the pixel matches the target color.
- Line 27: Logs the pixel match to
PixelEvaluation.txt. - Line 28: Ends the block for each dynamic location.
- Line 29: Ends the loop for dynamic location evaluations.
PIXEL RANGE
Purpose
The PIXEL RANGE object evaluates changes in a range of pixels within a defined screen area. It is ideal for monitoring dynamic screen content or detecting visual activity.
How It Works
- Monitors a defined rectangular area of the screen for pixel changes.
- Triggers actions when the specified number of pixel changes occur within the given timeout period.
- Supports custom delay settings between pixel change detections.
Parameters
- At Location [X:X Y:Y]::Size [W:Width H:Height]
- At Location: Specifies the screen area to monitor for pixel changes.
- X: The X-coordinate of the top-left corner of the pixel range.
- Y: The Y-coordinate of the top-left corner of the pixel range.
- Size: Defines the width and height of the pixel range.
- W: The width of the pixel range.
- H: The height of the pixel range.
- At Location: Specifies the screen area to monitor for pixel changes.
Operators for Evaluation
- CHANGES: Detects changes in the pixel range based on specified parameters.
- CHANGES::X::Y::Z:
- X: The number of changes to detect.
- Y: The total time to wait for changes (in seconds). A value of 0 waits until all changes occur. At the end of the time period, the statement will evaluate to FALSE and continue.
- Z: The delay between detecting pixel changes (in milliseconds). A value of 0 skips the delay.
- CHANGES::X::Y::Z:
![]()
Pixel Range condition via the 'Add Condition' dialog window.
![]()
Choose the Pixel Range dialog after selecting the PIXEL RANGE object.
Pixel Range Selection
- Move the mouse to the location of the start of the pixel range selection. The mouse position indicates the top-left most pixel.
- Use the
TABkey to enter theWidthandHeighttext boxes manually, or use theUP/DOWNkeyboard arrows to adjust theWidthandHeight. - Mouse over or click the
Size Grow +label to change the increment direction, or use theLeft/Rightkeyboard arrows. - Use the
TABkey to enter theLock Rangecheckbox and pressSPACEBARto lock in the pixel range. - When the pixel range selection is captured, press
ENTERor select theOKbutton.
Operator Examples
CHANGES:
1 | IF | PIXEL RANGE | At Location [X:2768 Y:602]::Size [W:100 H:50] | CHANGES::5::0::200 | MESSAGE PROMPT | Detected 5 changes in the pixel range.
Example: Pixel Range Monitoring
* | Start of macro: Monitors pixel ranges for changes and performs dynamic actions.
* | Step 1: Detect changes in a defined pixel range and log activity.
1 | IF | PIXEL RANGE | At Location [X=500 Y=200]::Size [W=300 H=150] | CHANGES::5::10::200 | THEN
* | Detected 5 changes within 10 seconds in the defined pixel range.
2 | RUN ACTION | MESSAGE PROMPT | Detected 5 changes in the pixel range at X=500, Y=200.
3 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelRangeLog.txt::APPEND_NEWLINE::5 changes detected in pixel range at %TIME% on %DATE%.
* | Further evaluation: Check another range if changes are detected here.
4 | IF | PIXEL RANGE | At Location [X=800 Y=400]::Size [W=200 H=100] | CHANGES::3::5::100 | THEN
5 | RUN ACTION | MESSAGE PROMPT | Additional activity detected in secondary pixel range at X=800 Y=400.
6 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelRangeLog.txt::APPEND_NEWLINE::Activity in secondary range at %TIME% on %DATE%.
7 | IF | END IF
8 | IF | ELSE
* | No changes detected in the initial range within the timeout period; log the inactivity.
9 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelRangeLog.txt::APPEND_NEWLINE::No changes detected in pixel range at %TIME% on %DATE%.
10 | IF | END IF
* | Step 2: Monitor a larger screen area for changes dynamically.
11 | FOR | EACH | I | = | 1 TO 3 | DO
* | Dynamically monitor three different screen areas sequentially.
12 | IF | PIXEL RANGE | At Location [X=%I%*100 Y=%I%*100]::Size [W=400 H=200] | CHANGES::2::8::500 | THEN
13 | RUN ACTION | MESSAGE PROMPT | Changes detected in area [%I%*100, %I%*100, W=400, H=200].
14 | RUN ACTION | OUTPUT TO FILE | D:\Logs\DynamicPixelRangeLog.txt::APPEND_NEWLINE::Changes detected in area [%I%*100 %I%*100] at %TIME%.
15 | IF | END IF
16 | FOR | NEXT
* | Step 3: Trigger specific actions based on pixel range activity.
17 | IF | PIXEL RANGE | At Location [X=100 Y=100]::Size [W=500 H=300] | CHANGES::4::15::0 | THEN
* | Trigger a specific action when changes are detected.
18 | RUN ACTION | MESSAGE PROMPT | High activity detected in monitored area!
19 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelRangeActivity.txt::APPEND_NEWLINE::High activity detected at %TIME% on %DATE%.
* | 20 | RUN ACTION | OUTPUT SCREENSHOT | D:\Screenshots\CapturedState_%TIME%.png
21 | IF | END IF
* | End of macro.
Explanation - Pixel Range Monitoring
- Line 1: Monitors the pixel range at
[X=500 Y=200]with size[W=300 H=150]for 5 changes within 10 seconds, with a delay of 200 ms between checks. - Line 2: Displays a message prompt if 5 changes are detected.
- Line 3: Logs the detected changes to
PixelRangeLog.txt. - Line 4: Checks a secondary pixel range at
[X=800 Y=400]with size[W=200 H=100]for 3 changes within 5 seconds and a 100 ms delay. - Line 5: Displays a message prompt if changes are detected in the secondary range.
- Line 6: Logs the detected activity in the secondary range to
PixelRangeLog.txt. - Line 7: Ends the evaluation for the secondary pixel range.
- Line 8: Begins the
ELSEblock if no changes are detected in the initial pixel range. - Line 9: Logs the inactivity in the pixel range to
PixelRangeLog.txt. Line 10: Ends the block for detecting changes in the initial pixel range.
- Line 11: Starts a loop to dynamically monitor three screen areas sequentially.
- Line 12: Monitors each dynamic area for 2 changes within 8 seconds, with a 500 ms delay between checks.
- Line 13: Displays a message prompt if changes are detected in the monitored area.
- Line 14: Logs the detected changes in the area to
DynamicPixelRangeLog.txt. - Line 15: Ends the block for detecting changes in a dynamic area.
Line 16: Ends the loop for dynamically monitoring pixel ranges.
- Line 17: Monitors a larger pixel range at
[X=100 Y=100]with size[W=500 H=300]for 4 changes within 15 seconds without delay. - Line 18: Displays a message prompt if high activity is detected.
- Line 19: Logs the detected activity to
PixelRangeActivity.txt. - Line 20: Captures a screenshot of the current screen state and saves it with a timestamped filename. (commented out - comming soon)
- Line 21: Ends the block for detecting high activity in the monitored range.
PIXEL VARIABLE
Purpose
The PIXEL VARIABLE object evaluates the difference between two defined pixel range variables. It is useful for detecting pixel range changes on the screen.
For detailed information on pixel variables, refer the the Pixel Variable page
How It Works
- Compares two pixel range variables previously declared using the
DEFINE PIXEL RANGE VARIABLEaction. - Triggers actions if the variables match or differ.
Declared Pixel Range Variables
When a pixel range is declared, it holds the current bitmap image within an internal pixel range bitmap array. Each pixel range variable includes the following properties:
%PIXEL_RANGE%: The internal pixel range array index number of the variable.%PIXEL_RANGE.XPOS%: The starting X position of the mouse.%PIXEL_RANGE.YPOS%: The starting Y position of the mouse.%PIXEL_RANGE.WIDTH%: The width of the pixel range bitmap.%PIXEL_RANGE.HEIGHT%: The height of the pixel range bitmap.%PIXEL_RANGE.TIME%: The time the pixel range was declared.%PIXEL_RANGE.DATE%: The date the pixel range was declared.
Operators for Evaluation
- MATCHES: Checks if two pixel variables are identical.
Operator Examples
MATCHES:
1 | IF | PIXEL VARIABLE | %BANNER_ORIGINAL% | MATCHES | %BANNER_NEW% | CONTINUE
Example: Pixel Variable Comparison
* | Start of macro: Define and compare pixel range variables.
* | Step 1: Define pixel range variables for comparison.
1 | RUN ACTION | DEFINE PIXEL RANGE VARIABLE | %BANNER_ORIGINAL%::At Location [X:50 Y:100 W:200 H:100]
2 | RUN ACTION | DEFINE PIXEL RANGE VARIABLE | %BANNER_NEW%::At Location [X:50 Y:100 W:200 H:100]
* | Step 2: Compare pixel range variables and evaluate their properties.
3 | IF | PIXEL VARIABLE | %BANNER_ORIGINAL% | MATCHES | %BANNER_NEW% | THEN
* | If pixel ranges match, notify the user and log details.
4 | RUN ACTION | MESSAGE PROMPT | Pixel ranges are identical.
5 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelVariableLog.txt::APPEND_NEWLINE::Pixel ranges match. Original range: %BANNER_ORIGINAL.XPOS%,%BANNER_ORIGINAL.YPOS%,%BANNER_ORIGINAL.WIDTH%,%BANNER_ORIGINAL.HEIGHT% at %BANNER_ORIGINAL.TIME%.
6 | IF | ELSE
* | If pixel ranges do not match, notify the user and log details.
7 | RUN ACTION | MESSAGE PROMPT | Pixel ranges differ.
8 | RUN ACTION | OUTPUT TO FILE | D:\Logs\PixelVariableLog.txt::APPEND_NEWLINE::Pixel ranges differ. New range: %BANNER_NEW.XPOS%,%BANNER_NEW.YPOS%,%BANNER_NEW.WIDTH%,%BANNER_NEW.HEIGHT% at %BANNER_NEW.TIME%.
9 | IF | END IF
* | End of macro.
Explanation - Pixel Variable Comparison
- Line 1: Defines the pixel range variable
%BANNER_ORIGINAL%for the area at[X:50 Y:100 W:200 H:100]. - Line 2: Defines the pixel range variable
%BANNER_NEW%for the same area[X:5 Y:100 W:200 H:100]. - Line 3: Compares the two pixel range variables
%BANNER_ORIGINAL%and%BANNER_NEW%using theMATCHESoperator. - Line 4: Displays a message prompt if the pixel ranges are identical.
- Line 5: Logs details of the matching pixel ranges to
PixelVariableLog.txt, including the position, dimensions, and timestamp of%BANNER_ORIGINAL%. - Line 6: Begins the
ELSEblock if the pixel ranges do not match. - Line 7: Displays a message prompt if the pixel ranges differ.
- Line 8: Logs details of the differing pixel ranges to
PixelVariableLog.txt, including the position, dimensions, and timestamp of%BANNER_NEW%. - Line 9: Ends the
IFblock for the pixel range comparison.
PROCESS ID
Purpose
The PROCESS ID object evaluates conditions based on the current status of a specific system process ID. It allows automation of actions related to running or missing processes.
How It Works
- Monitors the status of a specific process ID.
- Triggers actions based on whether the process exists or does not exist at the time of evaluation.
- A combo box is provided to select from the currently active system process IDs.
Parameters
- Process ID: The numerical identifier of the process to evaluate.
Operators for Evaluation
- EXIST: Checks if the process ID exists.
- NOT EXIST: Validates that the process ID does not exist.
Operator Examples
EXIST:
1 | IF | PROCESS ID | 12345 | EXIST | MESSAGE PROMPT | Process ID 12345 is active.NOT EXIST:
1 | IF | PROCESS ID | 67890 | NOT EXIST | RUN ACTION | OUTPUT TO FILE | C:\Logs\MissingProcess.txt::APPEND_NEWLINE::Process 67890 not running at %TIME%.
Example: Process ID Monitoring
* | Start of macro: Monitor process IDs and take relevant actions.
1 | IF | PROCESS ID | 12888 | EXIST | KILL PROCESS ID | 12888 | AND | 2 | IF | PROCESS ID | 12888 | NOT EXIST | MESSAGE PROMPT | Process 12888 successfully terminated.
3 | IF | PROCESS ID | 54321 | EXIST | RUN ACTION | MESSAGE PROMPT | Process ID 54321 is running and active.
4 | IF | PROCESS ID | 67890 | NOT EXIST | RUN ACTION | MESSAGE PROMPT | Process ID 67890 is not running. Starting critical task...
5 | RUN ACTION | RUN PROGRAM | C:\CriticalTask\Task.exe
Explanation - Process ID Monitoring
- Line 1: Checks if the process with ID
12888exists. If it does, terminates the process. - Line 2: Confirms that the process with ID
12888no longer exists after termination and notifies the user. - Line 3: Checks if the process with ID
54321exists and displays a message confirming it is running. - Line 4: Checks if the process with ID
67890does not exist. If not, notifies the user that the process is missing and prepares to start a critical task. - Line 5: Starts a critical task program if process ID
67890is not running.
PROCESS NAME
Purpose
The PROCESS NAME object evaluates conditions based on the current status of a specific system process name. It allows automation of actions related to processes identified by their names.
How It Works
- Monitors the status of a specific process name.
- Triggers actions based on whether the process exists or does not exist at the time of evaluation.
- A combo box is provided to select from the currently active system process names.
Parameters
- Process Name: The name of the process to evaluate.
Operators for Evaluation
- EXIST: Checks if the process name exists.
- NOT EXIST: Validates that the process name does not exist.
Operator Examples
EXIST:
1 | IF | PROCESS NAME | notepad | EXIST | SELECT WINDOW BY NAME | Untitled - NotepadNOT EXIST:
1 | IF | PROCESS NAME | explorer | NOT EXIST | RUN ACTION | MESSAGE PROMPT | Explorer process is not running.
Example: Process Name Monitoring
* | Start of macro: Evaluate the existence of processes by name.
1 | IF | PROCESS NAME | chrome | EXIST | THEN
* | Notify the user that Chrome is running.
2 | RUN ACTION | MESSAGE PROMPT | Chrome is running.
3 | IF | ELSE
* | Notify the user that Chrome is not running.
4 | RUN ACTION | MESSAGE PROMPT | Chrome is not running.
5 | IF | END IF
6 | IF | PROCESS NAME | firefox | NOT EXIST | THEN
* | Notify the user that Firefox is not found.
7 | RUN ACTION | MESSAGE PROMPT | Firefox is not running.
8 | IF | END IF
Explanation - Process Name Monitoring
- Line 1: Checks if the process
chromeexists on the system. - Line 2: Displays a message prompt if Chrome is running.
- Line 3: Begins the
ELSEblock for when Chrome is not running. - Line 4: Displays a message prompt if Chrome is not running.
- Line 5: Ends the block for checking Chrome’s existence.
- Line 6: Checks if the process
firefoxdoes not exist on the system. - Line 7: Displays a message prompt if Firefox is not running.
- Line 8: Ends the block for checking Firefox’s existence.
RECEIVE UDP PACKET STRING
Purpose
The RECEIVE UDP PACKET STRING object evaluates conditions based on the contents of UDP packets received during macro execution. This feature enables Mini Mouse Macro to interact with networked systems by responding to specific UDP strings.
Parameters
- Source::Port::Expected String::Timeout:
- Source: The IP address of the sender (or
ANYfor all sources). - Port: The UDP port number to listen on.
- Expected String: The string to match within the received packet.
- Timeout: The duration (in milliseconds) to wait for the string before timing out.
- Source: The IP address of the sender (or
How It Works
- Listens for UDP packets on a specified port.
- Reads the string content of the packet.
- Triggers actions if the packet contains the expected string.
Operators for Evaluation
- STRING FOUND: Validates if the specified string is found in the UDP packet.
Operator Examples
STRING FOUND:
1 | IF | RECEIVE UDP PACKET STRING | ANY::41414::StartMacro4::20000 | STRING FOUND | SEND UDP PACKET STRING | 192.168.0.2::41414::LoadMacro5- If a packet containing
StartMacro4is received on port41414from any source within20 seconds, sends a UDP packet withLoadMacro5to192.168.0.2on port41414.
- If a packet containing
Example: Network Triggered Macro Execution
* | Start of macro: Listen for specific UDP packets and respond dynamically.
* | Step 1: Listen for a start command on port 5050 from any source.
1 | IF | RECEIVE UDP PACKET STRING | ANY::5050::StartTask::20000 | STRING FOUND | THEN
* | Received StartTask command; load and execute a macro.
2 | RUN ACTION | LOAD MACRO | C:\Macros\TaskAutomation.mmmacro
3 | RUN ACTION | MESSAGE PROMPT | StartTask command received from ANY source.\nMacro execution initiated successfully.::Start Task Received::0::Information
4 | IF | ELSE
* | No StartTask command received within the timeout; notify the user.
5 | RUN ACTION | MESSAGE PROMPT | StartTask command was not received within the timeout period.\nPlease check the network configuration.::Timeout Alert::10::Exclamation
6 | IF | END IF
* | Step 2: Listen for an alert from a specific IP on port 6060.
7 | IF | RECEIVE UDP PACKET STRING | 192.168.1.10::6060::Alert::10000 | STRING FOUND | THEN
* | Received Alert packet; notify the user and provide details.
8 | RUN ACTION | MESSAGE PROMPT | Alert received from 192.168.1.10 on port 6060.\n\nAction: Log off initiated at %TIME% on %DATE%.::Critical Alert Received::0::Critical
9 | RUN ACTION | LOG OFF COMPUTER
10 | IF | ELSE
* | Alert not received; log inactivity and display a reminder.
11 | RUN ACTION | MESSAGE PROMPT | No alert packet received from 192.168.1.10 within the timeout.\n\nMonitor network activity for anomalies.::Alert Not Received::0::Information
12 | IF | END IF
* | End of macro.
Explanation - Network Triggered Macro Execution
- Line 1: Listens for a UDP packet containing
StartTaskfrom any source on port 5050 within 20 seconds. - Line 2: Loads the macro
TaskAutomation.mmmacroif theStartTaskpacket is received. - Line 3: Displays an information-style message box confirming receipt of the StartTask command and successful macro initiation.
- Line 4: Begins the
ELSEblock for when noStartTaskpacket is received within the timeout. - Line 5: Displays an exclamation-style message box alerting the user of the timeout and suggesting a network configuration check, with a 10-second timeout for the prompt.
Line 6: Ends the block for listening on port 5050.
- Line 7: Listens for a UDP packet containing
Alertfrom IP192.168.1.10on port 6060 within 10 seconds. - Line 8: Displays a critical-style message box providing details of the received alert and the subsequent log-off action, including the current time and date.
- Line 9: Logs off the computer as a response to the alert.
- Line 10: Begins the
ELSEblock for when noAlertpacket is received within the timeout. - Line 11: Displays an information-style message box notifying the user that no alert was received, with a reminder to monitor network activity.
- Line 12: Ends the block for listening on port 6060.
STRING VARIABLE
Purpose
The STRING VARIABLE object evaluates conditions based on the value of string variables in use within Mini Mouse Macro. String variables allow dynamic manipulation of text during macro execution, enhancing flexibility and control.
For detailed information on string variables, refer the the String Variable page
How It Works
- String variables are defined using the
DEFINE STRING VARIABLEaction. - Variables can contain static or dynamic text values.
- Strings are evaluated for exact matches, substring occurrences, or inequality during macro execution.
- They support complex constructs for advanced workflows.
Parameters
- Variable Name: The name of the string variable, which can be the default
%STRING%or a custom name. - Value: The value assigned to or evaluated within the string variable.
Custom Names
Custom string variable names allow for meaningful identification of values within macros. Examples include:
1 | RUN ACTION | DEFINE STRING VARIABLE | %NAME%::Kirstin
2 | RUN ACTION | DEFINE STRING VARIABLE | %CITY%::Townsville
3 | RUN ACTION | DEFINE STRING VARIABLE | %COUNTRY%::Australia
In these examples, %NAME%, %CITY%, and %COUNTRY% are custom variables with descriptive names.
Complex String Constructs
String variables can be incorporated dynamically into macro entries, providing greater control during execution. This supports advanced use cases like combining variables or iterative operations.
Consider the following example:
* | This macro increments mouse X and Y positions 100 times.
1 | RUN ACTION | DEFINE INTEGER VARIABLE | %INTEGER1%::0
2 | RUN ACTION | DEFINE STRING VARIABLE | %STRING1%::Mouse Movement
3 | %INTEGER1% | %INTEGER1% | %INTEGER2% | %STRING1%
4 | RUN ACTION | DEFINE INTEGER VARIABLE | %INTEGER1%::+1
5 | IF | INTEGER VARIABLE | %INTEGER1% | < | 100 | GOTO MACRO LINE | 3 | ELSE | 6 | RUN ACTION | MESSAGE PROMPT | Mouse Moved 100 times::END
In this example, multiple variables collaborate to iterate mouse movements dynamically.
String Output
String variables can be embedded directly into actions or outputs, enabling dynamic behavior.
For example:
1 | RUN ACTION | DEFINE STRING VARIABLE | %MESSAGE%::Welcome to Mini Mouse Macro
2 | RUN ACTION | MESSAGE PROMPT | %MESSAGE%
The macro outputs the value of %MESSAGE%, dynamically displaying “Welcome to Mini Mouse Macro” in a message prompt.
Operators for Evaluation
- IS: Checks if the string variable matches a specified value.
- IS NOT: Validates that the string variable does not match the specified value.
- CONTAINS: Confirms if the string variable contains a substring.
Operator Examples
IS:
1 | IF | STRING VARIABLE | %STRING% | IS | "Macro1" | RUN ACTION | MESSAGE PROMPT | Exact match found.IS NOT:
1 | IF | STRING VARIABLE | %STRING% | IS NOT | "Macro2" | RUN ACTION | OUTPUT TO FILE | C:\Logs\MacroLog.txt::APPEND_NEWLINE::%STRING% did not match Macro2.CONTAINS:
1 | IF | STRING VARIABLE | %STRING% | CONTAINS | "Start" | RUN ACTION | DEFINE STRING VARIABLE | %STRING%::Starting Process
Example: Dynamic String Evaluation
* | Start of macro: Dynamically handle user tasks based on the system environment and date.
* | Step 1: Define a custom string variable for user-specific greeting.
1 | RUN ACTION | DEFINE STRING VARIABLE | %GREETING%::Welcome, %ENV_USERNAME%! Today is %DATE_DDDD%, %DATE_MMMM% %DATE_DD%, %DATE_YYYY%.
* | Step 2: Display the dynamic greeting to the user.
2 | RUN ACTION | MESSAGE PROMPT | %GREETING%.\nYour home directory is %ENV_USERPROFILE%.\nSystem time: %TIME%.::Dynamic Greeting::0::Information
* | Step 3: Perform actions based on the weekday.
3 | IF | STRING VARIABLE | %DATE_DDDD% | IS | Monday | THEN
* | If it’s Monday, prepare a weekly report and notify the user.
4 | RUN ACTION | MESSAGE PROMPT | Happy Monday!\nStarting weekly report generation.::Weekly Report::0::Information
5 | RUN ACTION | RUN PROGRAM | C:\Program Files\ReportGenerator\WeeklyReport.exe
6 | IF | ELSE
* | For other days, display a motivational quote and log activity.
7 | RUN ACTION | DEFINE STRING VARIABLE | %QUOTE%::“The best way to predict the future is to invent it.” - Alan Kay
8 | RUN ACTION | MESSAGE PROMPT | Today’s Quote:\n%QUOTE%::Motivational Quote::0::Information
9 | RUN ACTION | OUTPUT TO FILE | C:\Logs\DailyLog.txt::APPEND_NEWLINE::User %ENV_USERNAME% logged in on %DATE_DDDD%, %DATE_MMMM% %DATE_DD%, %DATE_YYYY% at %TIME%.
10 | IF | END IF
* | End of macro.
Explanation - Dynamic String Evaluation
- Line 1: Defines a custom string variable
%GREETING%with a dynamic greeting, including the current username, date, and time. - Line 2: Displays an information-style message box with the dynamic greeting and system details such as the home directory and current time.
- Line 3: Checks if the current day of the week (
%DATE_DDDD%) is Monday. - Line 4: If it’s Monday, displays an information-style message box notifying the user about weekly report generation.
- Line 5: Launches the Weekly Report Generator program.
- Line 6: Begins the
ELSEblock for non-Monday days. - Line 7: Defines a motivational quote as a string variable
%QUOTE%. - Line 8: Displays the motivational quote in an information-style message box.
- Line 9: Logs the user’s login details, including the current date and time, to
DailyLog.txt. - Line 10: Ends the block for non-Monday actions.
TCP PORT OPEN
Purpose
The TCP PORT OPEN object evaluates conditions based on the state of a specified TCP port on a remote or local host. It determines whether the port is open or closed by attempting to establish a connection.
How It Works
- Initiates a connection to the target host on the specified TCP port.
- If the connection succeeds within the timeout period, the port is considered open.
- If the connection fails or times out, the port is considered closed.
Parameters
- Host: The IP address or hostname of the target system.
- Port: The TCP port number to check.
- Timeout: The duration (in milliseconds) to wait for a response before considering the port closed.
Operators for Evaluation
- IS OPEN: Validates that the TCP port is open.
- IS CLOSED: Confirms that the TCP port is closed.
Operator Examples
IS OPEN:
1 | IF | TCP PORT OPEN | 192.168.0.2::41414::200 | IS OPEN | SEND UDP PACKET STRING | 192.168.0.2::41414::LoadMacro5- Checks if port
41414is open on192.168.0.2with a timeout of200 ms. If open, sends a UDP packet containingLoadMacro5.
- Checks if port
IS CLOSED:
1 | IF | TCP PORT OPEN | 127.0.0.1::80::100 | IS CLOSED | MESSAGE PROMPT | The local web server on port 80 is CLOSED::Port Closed- Verifies if port
80on the local host (127.0.0.1) is closed within100 ms. If closed, displays a message prompt.
- Verifies if port
Example: Port State Monitoring
* | Start of macro: Monitor TCP port states and trigger dynamic responses.
* | Step 1: Check if a remote TCP port is open.
1 | IF | TCP PORT OPEN | 192.168.1.100::22::200 | IS OPEN | THEN
* | SSH port is open on the remote server; notify the user and perform a secure file transfer.
2 | RUN ACTION | MESSAGE PROMPT | SSH port (22) on 192.168.1.100 is OPEN.\nInitiating secure file transfer...::SSH Port Open::0::Information
3 | RUN ACTION | RUN PROGRAM | C:\Tools\SFTPClient.exe /host=192.168.1.100 /port=22 /user=%ENV_USERNAME%
4 | IF | ELSE
* | SSH port is closed; notify the user and log the incident.
5 | RUN ACTION | MESSAGE PROMPT | SSH port (22) on 192.168.1.100 is CLOSED.\nPlease check the server or network configuration.::SSH Port Closed::10::Exclamation
6 | IF | END IF
* | Step 2: Check if the local web server port is closed.
7 | IF | TCP PORT OPEN | 127.0.0.1::80::100 | IS CLOSED | THEN
* | Local web server port 80 is closed; start the server and notify the user.
8 | RUN ACTION | RUN PROGRAM | C:\WebServer\start.bat
9 | RUN ACTION | MESSAGE PROMPT | Local web server on port 80 was CLOSED.\nStarting the server now.::Web Server Start::0::Information
10 | IF | END IF
* | End of macro.
Explanation - Port State Monitoring
- Line 1: Checks if TCP port 22 (SSH) on the remote server
192.168.1.100is open, with a timeout of 200 ms. - Line 2: Displays an information-style message box if the port is open, notifying the user of the SSH connection.
- Line 3: Runs an SFTP client program to initiate a secure file transfer to the remote server.
- Line 4: Begins the
ELSEblock if the port is not open. - Line 5: Displays an exclamation-style message box if the port is closed, advising the user to check the server or network.
Line 6: Ends the block for checking the SSH port.
- Line 7: Checks if TCP port 80 (HTTP) on the local machine is closed, with a timeout of 100 ms.
- Line 8: Starts the local web server by running a batch file if the port is closed.
- Line 9: Displays an information-style message box notifying the user that the web server has been started.
- Line 10: Ends the block for checking the local web server port.
TIME
Purpose
The TIME object evaluates conditions based on the current system time. It is used for scheduling or triggering macro actions at specific times.
How It Works
- Compares the current system time with a specified time.
- Triggers actions if the condition evaluates to true.
- Uses a 12-hour format for time values (e.g.,
2:00:56 PM).
Parameters
- Time Value: The target time to evaluate.
Operators for Evaluation
- IS: Validates that the current system time matches the specified time.
- IS NOT: Confirms that the current system time does not match the specified time.
- IS BEFORE CURRENT TIME: Checks if the specified time is before the current system time.
- IS AFTER CURRENT TIME: Checks if the specified time is after the current system time.
Operator Examples
IS:
1 | IF | TIME | 2:00:56 PM | IS | CONTINUE- Triggers the macro to continue if the system time is
2:00:56 PM.
- Triggers the macro to continue if the system time is
IS BEFORE CURRENT TIME:
1 | IF | TIME | 2:04:09 PM | IS BEFORE CURRENT TIME | GOTO MACRO LINE | 1- Redirects the macro to line
1if the time is before2:04:09 PM.
- Redirects the macro to line
IS AFTER CURRENT TIME:
1 | IF | TIME | 2:07:10 PM | IS AFTER CURRENT TIME | RESTART COMPUTER- Restarts the computer if the current time is after
2:07:10 PM.
- Restarts the computer if the current time is after
Example: Time-Based Actions
1 | IF | TIME | 9:00:00 AM | IS | RUN ACTION | MESSAGE PROMPT | Good morning! It's 9:00 AM.
2 | IF | TIME | 5:00:00 PM | IS AFTER CURRENT TIME | RUN ACTION | SHUTDOWN COMPUTER
TIME AND DATE
Purpose
The TIME AND DATE object evaluates conditions based on the current system time and date. It provides precise control for actions requiring both time and date matching.
How It Works
- Compares the current system time and date with a specified value.
- Triggers actions if the condition evaluates to true.
- Uses the format
HH:MM:SS DDMonYYYY(e.g.,14:25:30 25Jun2025).
Parameters
- Time and Date Value: The target time and date to evaluate.
Operators for Evaluation
- IS: Validates that the current system time and date match the specified value.
- IS NOT: Confirms that the current system time and date do not match the specified value.
- IS BEFORE CURRENT DATE & TIME: Checks if the specified time and date are before the current system time and date.
- IS AFTER CURRENT DATE & TIME: Checks if the specified time and date are after the current system time and date.
Operator Examples
IS:
1 | IF | TIME AND DATE | 14:25:30 25Jun2025 | IS | CONTINUE- Continues the macro if the system time and date match
14:25:30 25Jun2025.
- Continues the macro if the system time and date match
IS BEFORE CURRENT DATE & TIME:
1 | IF | TIME AND DATE | 14:25:30 25Jun2025 | IS BEFORE CURRENT DATE & TIME | WAIT HOURS | 12- Waits for 12 hours if the time and date are before
14:25:30 25Jun2025.
- Waits for 12 hours if the time and date are before
IS AFTER CURRENT DATE & TIME:
1 | IF | TIME AND DATE | 14:30:00 25Jun2025 | IS AFTER CURRENT DATE & TIME | DEFINE STRING VARIABLE | 14:30_25 JUNE 2025- Defines a string variable if the time and date are after
14:30:00 25Jun2025.
- Defines a string variable if the time and date are after
Example: Combined Time and Date Actions
* | Start of macro: Perform actions based on current time, date, and time-and-date.
* | Step 1: Check if the time is 9:00:00 AM.
1 | IF | TIME | 9:00:00 AM | IS | THEN
* | Notify the user to start their daily tasks.
2 | RUN ACTION | MESSAGE PROMPT | Good morning! It's 9:00 AM.\nTime to start your daily tasks.::Daily Reminder::0::Information
3 | IF | END IF
* | Step 2: Check if the current date is the first day of the month.
4 | IF | DATE | 1/%DATE_MM%/%DATE_YYYY% | IS | THEN
* | If it's the first day of the month, run the monthly report generator.
5 | RUN ACTION | MESSAGE PROMPT | Today is %DATE_DDDD%, %DATE_MMMM% 1.\nMonthly report generation initiated.::Monthly Report::0::Information
6 | RUN ACTION | RUN PROGRAM | C:\Tools\MonthlyReportGenerator.exe
7 | IF | END IF
* | Step 3: Check if the current time and date are after a specific schedule.
8 | IF | TIME AND DATE | 10:30:00 3Jan2025 | IS AFTER CURRENT DATE & TIME | THEN
* | Schedule a system restart after hours if the condition is true.
9 | RUN ACTION | MESSAGE PROMPT | Scheduled maintenance at 10:30 AM on 3 Jan 2025.\nRestarting system now.::Scheduled Restart::0::Critical
10 | RUN ACTION | RESTART COMPUTER
11 | IF | ELSE
* | Notify the user that the scheduled time has passed.
12 | RUN ACTION | MESSAGE PROMPT | Scheduled maintenance time has passed.\nPlease reschedule.::Schedule Missed::10::Exclamation
13 | IF | END IF
* | End of macro.
Explanation - Combined Time and Date Actions
- Line 1: Checks if the current time is exactly 9:00:00 AM.
- Line 2: Displays an information-style message box reminding the user to start their daily tasks if the condition is met.
Line 3: Ends the block for the time-based daily reminder.
- Line 4: Checks if the current date is the first day of the month.
- Line 5: Displays an information-style message box notifying the user about monthly report generation.
- Line 6: Runs the Monthly Report Generator program if the condition is met.
Line 7: Ends the block for the monthly report scheduler.
- Line 8: Checks if the current time and date are after
10:30:00 AM on 3 Jan 2025. - Line 9: Displays a critical-style message box notifying the user about system restart for scheduled maintenance.
- Line 10: Restarts the computer to perform maintenance if the condition is true.
- Line 11: Begins the
ELSEblock for when the scheduled time has passed. - Line 12: Displays an exclamation-style message box notifying the user that the scheduled time has passed and rescheduling is needed.
- Line 13: Ends the block for the time-and-date-based maintenance scheduler.
WINDOW TITLE
Purpose
The WINDOW TITLE object evaluates a condition based on the presence of a specific window title. This is useful for determining if a program window is open and triggering actions accordingly.
How It Works
window with the specified title exists or does not exist.
- Checks if a window with the specified title exists or does not exist.
- Triggers actions such as selecting the window or running a program based on the evaluation result.
Parameters
window with the specified title exists or does not exist.
- Window Title: The title of the window to evaluate.
Operators for Evaluation
window with the specified title exists or does not exist.
- EXIST: Confirms that a window with the specified title is open.
- NOT EXIST: Validates that no window with the specified title is open.
Operator Examples
EXIST:
1 | IF | WINDOW TITLE | index.txt - Notepad | EXIST | SELECT WINDOW BY NAME | index.txt - Notepad- Selects the window titled
index.txt - Notepadif it exists.
- Selects the window titled
NOT EXIST:
1 | IF | WINDOW TITLE | Untitled - Notepad | NOT EXIST | RUN ACTION | RUN PROGRAM | D:\Macro\index.txt- Opens the file
index.txtin Notepad if the window titledUntitled - Notepaddoes not exist.
- Opens the file
Example: Window Title-Based Actions
* | Start of macro: Manage the Notepad window dynamically based on its title.
* | Step 1: Check if a Notepad window with the title `index.txt - Notepad` is open.
1 | IF | WINDOW TITLE | index.txt - Notepad | EXIST | THEN
* | If the window exists, bring it to the foreground and display its status.
2 | RUN ACTION | SELECT WINDOW BY NAME | index.txt - Notepad
3 | RUN ACTION | MESSAGE PROMPT | The file 'index.txt' is already open in Notepad.\nBringing it to the foreground.::Window Found::0::Information
4 | IF | ELSE
* | If the window doesn't exist, open the file in Notepad and notify the user.
5 | RUN ACTION | RUN PROGRAM | notepad.exe D:\Macro\index.txt
6 | RUN ACTION | MESSAGE PROMPT | The file 'index.txt' was not open.\nIt has now been opened in Notepad.::Window Opened::0::Information
7 | IF | END IF
Explanation - Window Title-Based Actions
- Line 1: Checks if a window with the title
index.txt - Notepadexists. - Line 2: If the window exists, selects the window by its name and brings it to the foreground.
- Line 3: Displays an information-style message box confirming that the file is already open and brought to the foreground.
- Line 4: Begins the
ELSEblock for when the window does not exist. - Line 5: Opens the file
index.txtin Notepad using theRUN PROGRAMaction. - Line 6: Displays an information-style message box notifying the user that the file has been opened in Notepad.
- Line 7: Ends the block for checking the window title condition.